Threat modeling is a process for optimizing application, business, or system processes by identifying potential threats and vulnerabilities, and establishing countermeasures to prevent or lessen the effects of those threats to the system.
Five Major Threat Modeling Steps:
- Defining security requirements
- Creating an application diagram
- Identifying threats
- Mitigating threats
- Validating that the threats have been mitigated
Threat modeling works by identifying the various types of threat agents that could possibly cause harm to an application and/or computer system, and adopts the perspective of hackers to see how much damage the threats can cause.
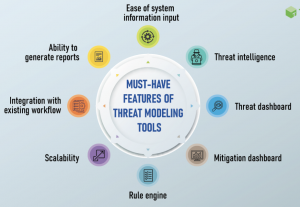
Great Threat Modeling overview.
The list and the diagram make it extremely easy to understand.