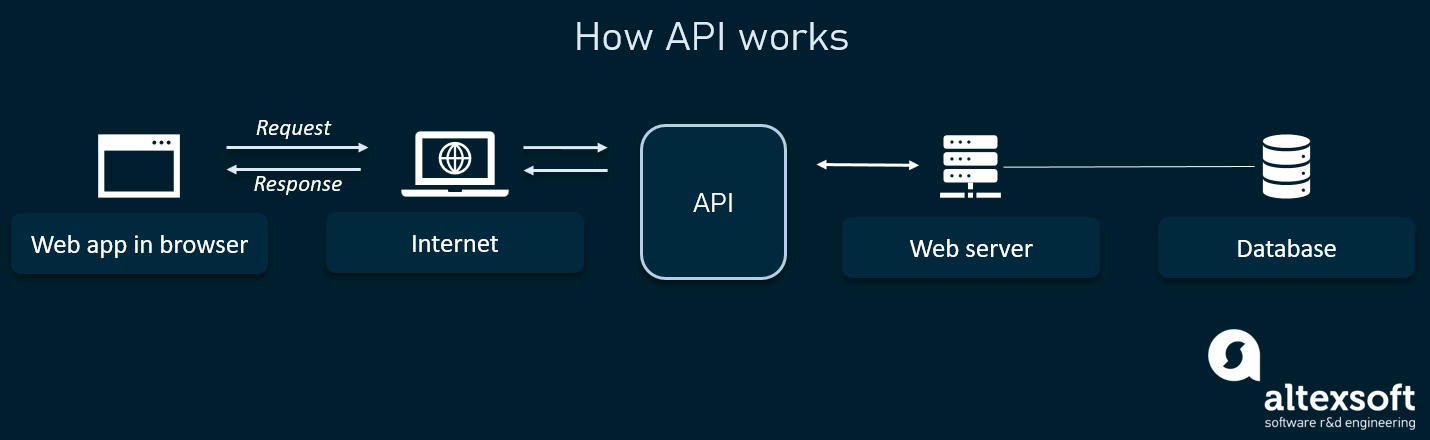
Threat modeling is one of the most important components of staying secure online. It is essentially the process of deciding what data you want to protect and who you’re trying to protect it from. It is figuring out what you are most worried about being hacked. To attempt to keep information secure online, the government has placed regulations involving data protection and cybersecurity. Some of these regulations include the California Consumer Privacy Act (CCPA), which is a regulation for privacy and personal data protection. Some more government cybersecurity regulations include: Health Insurance Portability and Accountability Act (HIPAA), Gramm-Leach-Bliley Act, and the 2002 Homeland Security Act which includes the Federal Information Security Management Act (FISMA). One way data can be breached is through ransomware. Ransomware is a type of malware from crypto-virology that threatens to publish the victim’s personal data or perpetually block access to it unless a ransom is paid, usually in Bitcoin. Hospitals are often a main target of ransomware because they provide critical care and rely on up-to-date information from patient records. Without quick access to their patients records such as drug histories, surgery directive and other information, patient care can get delayed, causing the hospital to likely pay the ransom rather than risk delays that could result in death and lawsuits. Although data breaches can sometimes be inevitable, there are ways you can protect yourself online. Some of these can include: Ad blockers, antivirus’s, avoiding dogs plug-ins, back-up files, disabling macros, firewalls, and VPN’s. Protecting yourself online is very important in ensuring your data and personal information is not leaked. In class, we downloaded the software 1Password, which is a password manager to help keep your data secure. It lets you know if your password is strong enough or if it needs to be changed. Aside from data security, another interesting relatively new form of technology is becoming increasingly popular, artificial intelligence. Artificial Intelligence (AI) is the ability of a computer or a robot controlled by a computer to do tasks that are usually done by humans because they require human intelligence and discernment. The three main types of AI’s include narrow (ANI), general (AGI), and super intelligence (ASI). an ANI is one of the more commonly used AI’s, appearing in all computers. The most commonly used ANI’s is Siri in Apple products. AGI is the type of adaptable intellect found in humans, a flexible form of intelligence capable of learning how to carry out vastly different tasks, which can include anything from haircutting or reasoning about a wide variety of topics based on its accumulated experience. ASI is described as any intellect that greatly exceeds the cognitive performance of humans in virtually all domains of interest. Alan Turing is known as the father of AI and computer science. He was a cryptanalysis during WWII, and cracked the code that enabled the allies victory. He founded the Turing test, which is a method of inquiry in AI for determining whether or not a computer is capable of thinking like a human being.