Wireshark Install:
- The latest copy of the wireshark can be obtained from wireshark.org
- Download and install the copy of the wireshark that is relevant to the operating system you are using. There is no preference for the use of Wireshark, but you must be familiar with the OS you are using.
- Please ensure that you have “winpcap” installed during your install. It is crucial for the proper packet capture.
- Detailed directions for Wireshark install is available here: https://www.wireshark.org/docs/wsug_html_chunked/ChapterBuildInstall.html
- Once you are ready to start please ensure that you run wireshark as an Without it, you may not have enough privileges to capture packet data.
- Once the packet capture screen appears, you should see the following screen or something similar.
- Select the interface that you are noticing traffic on.
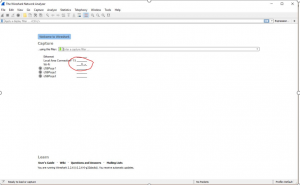
- Often you can establish a capture filter to eliminate any unwanted traffic. But keep in mind that when you do that, you are not capturing everything. You may miss something that you require. You can also use display filter, which allows you to filter out what you don’t want to see. This way you are still capturing the traffic but not actually seeing it.
- While the wireshark is running a capture, open a shell or a command prompt.
- Ping a well known DNS name and or server. (run it continuously)
- In wireshark – use a display filter : filtering on ICMP
- You will notice that when there is an error, packet may be colored black. You can actually establish your own color scheme or use the default.
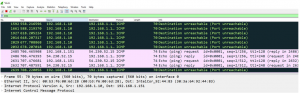
- Color scheme can be established under “preferences / appearance” doing so will facilitate your ability to use wireshark more easily.
- Now lets explore the ICMP packet more closely: (Echo Request)
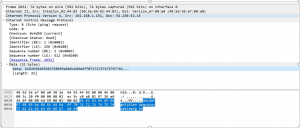
- The following list describes the elements in the ICMP header
- Type – ICMP has different types of messages such as Type 8 – echo request
- Code – This 8 bit value provides further information about some types of ICMP packets
- Checksum – 16 bit – error checking data
- Identifier – (BE) ICMP ID Numbers
- Identifier – (LE) Little Endian – stores least significant byte first
- Sequence Number – (BE) ICMP Packet sequence
- Sequence Number – (LE) ICMP Packet Sequence
- (Note: Identifier – This is set in the request packet, and echoed back in the reply, to be able to keep different ping requests and replies together.
Sequence number – The sequence number for each host, generally this starts at 1 and is incremented by 1 for each packet. )
- Response IN – field indicates receipt of response and the packet number of the response.
- Data : Actual data the packet is communicating.
Lab 1: Basics
Familiarize yourself with the use of color schemes and display filters.
- Make sure you are still capturing traffic
- Visit a website -> Your choice
- Go Back to wireshark -> Identify the TCP SYN traffic that is generated for the website you visited.
- Save the wirecapture and provide a name for the pcap file. “YourName_Lab1”
Answer the following questions:
Packet number of the “Initial SYN” request
Website you visited: ________________
Provide a screen capture of the traffic conversation