This article talks about how the NSA allegedly snooped on VPN traffic by exploiting a vulnerability in the CISCO PIX VPN> The versions that are vulnerable are 5.3(9) through 6.3(4) and were supported by CISCO from 2002 to 2009. The attack code was dubbed BenignCertain and exploits a vulnerability in Cisco’s implementation of the Internet Key Exchange, a protocol that uses digital certificates to establish a secure connection between two parties. The packets cause the vulnerable device to return a chunk of memory. A parser tool included in the exploit is then able to extract the VPN’s pre-shared key and other configuration data out of the response. According to one of the researchers who helped confirm the exploit, it works remotely on the outside PIX interface. This means that anyone on the Internet can use it. No pre-requirements are necessary to make the exploit work. The exploit helps explain documents leaked by NSA contractor Edward Snowden and cited in a 2014 article that appeared in Der Spiegel. The article reported that the NSA had the ability to decrypt more than 1,000 VPN connections per hour. The revelation is also concerning because data returned by the Shodan search engine indicate more than 15,000 networks around the world still use PIX, with the Russian Federation, the US, and Australia being the top three countries affected. The following is a screen shot of BenignCertain extracting a shared key from a Cisco PIX firewall.
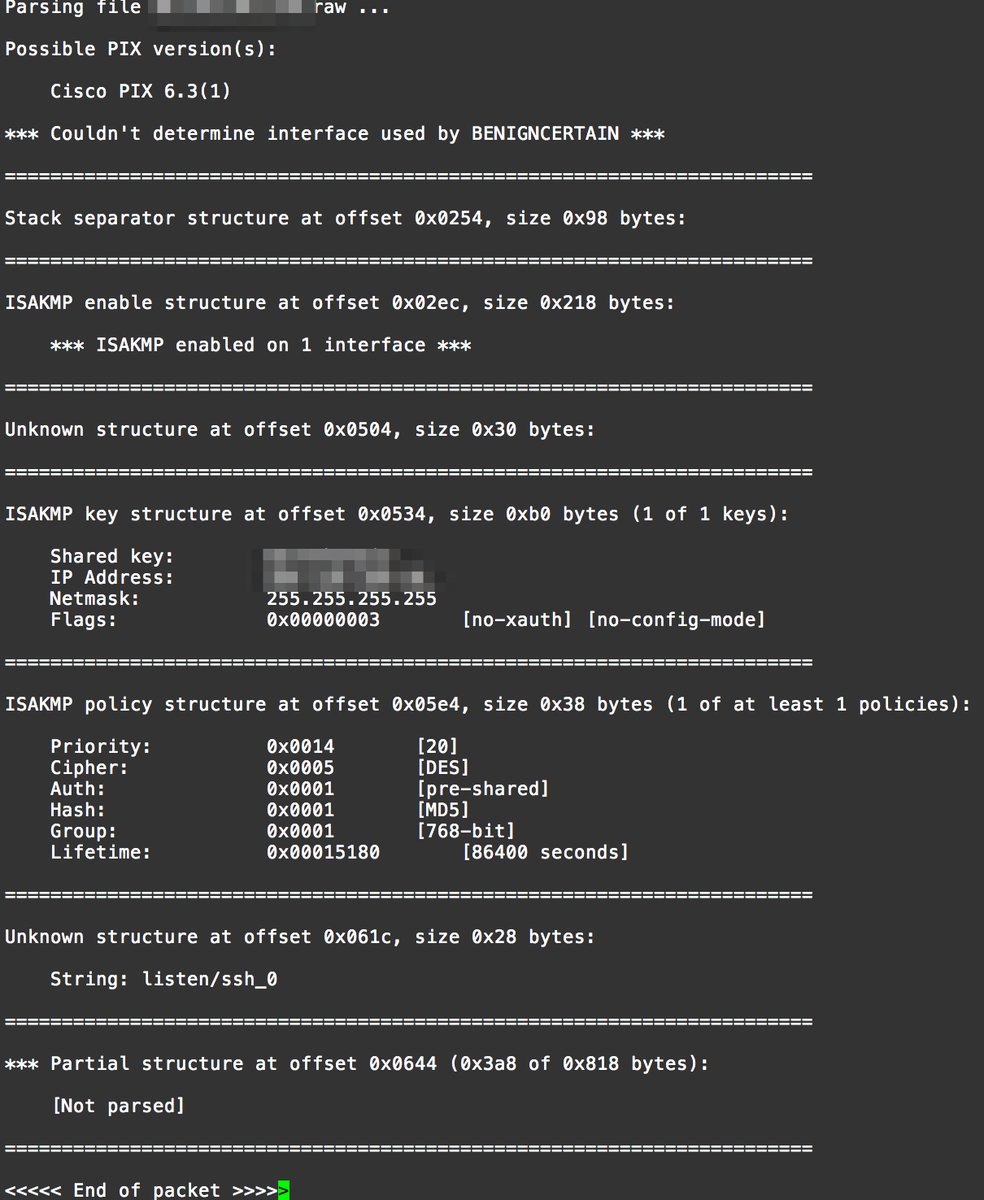
View article here.
Interesting articles Bilaal. It’s very concerning that so many security products are becoming subject to these vulnerabilities and exploits, especially when we find out that they’ve been exploited for many years. It really shows the importance of secure product development (on the vendor side) and due diligence in software selection (on the customer side).
It also makes me wonder if these vulnerabilities were intentionally planted by developers as “back doors”.
Good point Jason, I wasn’t thinking along those lines but it is quite possible that the vulnerability was intentionally planted as a back door..