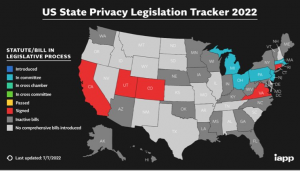
There are so many people in the U.S., and each person has important personal data. In order to keep their information private and secure, there are a few regulations in place. In terms of privacy and personal data, there is the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR). Surprisingly, even though technology is so vast, there aren’t that many federal laws covering cybersecurity. The ones that do exist include the Gramm-Leach-Bliley Act (1999), the 2002 Homeland Security Act, which includes the Federal Information Security Management Act, and the Health Insurance Portability and Accountability Act (HIPAA), created in 1996. There are also some bills being enacted at the state level, but according to the map that we looked at in class, many states do not have regulations established. The states that I do see with signed statutes/bills (indicated in red) are California, Utah, Colorado, Virginia, and Connecticut. For Pennsylvania, it looks like we have something in committee, indicated by the light blue.
Hey Madeline,
I think you did a great explanation of how important is to protect your personal data. I have 2FA turned on all my social media accounts. I think it is super important to secure and protect any account that you may have. I have an authentication app for all of my passwords for security purposes.