A variable in java script is a location for date storage. There are two types of variables that are renowned in java script which are global variables and local variables. In javascript, a variable is created when you combine the word let with the data that you are trying to decipher. In order to initialize a variable in javascript, one must first use the type followed by the variable, an equal sign and lastly the expression. the difference between initialization and declaration in variables is that declaration declares how the creation of variables is met while initialization helps to initiate the values use of variables. When naming a variable in javascript one must start off the sequence with a lowercase letter and then followed by capitalizing the first letter of the following words. When using Java script, the arithmetic operators are distinguished through numerical values such as variables or literals. They are returned as a single numerical value but the main symbols used are the subtraction, division, multiplication and addition symbols. These arithmetic operators help to create a sequence/formula on javascript. Concatenation in Javascript is the operation to join more than two strings to give a one finalized result. The two concatenation operators used is javascript are the + and the +=. Lastly, javascript used the prompt () as a way to prompt a user for a response. This helps to get the users input on the code.
Posts
The Purpose of If/Else Statements (6A)
If/else statements are used to figure out if a condition is true or false. They play an important role when there are multiple decisions involved. An if/else statement is basically set up like this:
if (something_is_true) {
do something;
} else {
do_something_different;
}
The word “if” is used to identify the expression that will be evaluated. In addition, “else” is used to identify what will happen whether the expression is true or false (the decisions that are involved in the process). The program will run through the statement and check if the initial statement is true. If not, it will move on to the first else statement. It will go down the list until it reaches something that meets the criteria of the if statement. If/else statements can sometimes get confused with else/if statements. Although they do sound similar, there is a difference. An else/if statement is when you have an if/else statement within another. For example:
if (position = 200) && (position < 300)) {
alert (“Do something else!”);
} else {
alert (“Do something even more different!”);
}
JavaScript Functions (5B)
A Javascript function groups a combination of statements together and makes your code reusable. Functions can also be applied to math problems, such as finding the sum of a group of numbers or solving for distance in an equation. The majority of work will be contained in functions while the main program is just handling input and output. Every Javascript function is the same in that they all are passed zero or more pieces of information, have a name, and, normally, return a value. Excel functions, on the other hand, will return a value no matter what. There are a few extra steps when writing functions in Javascript. They require more parentheses as well as brackets. Similar to variables, we can’t just name, or define, our function and leave it like that. It needs to be called. Normally, the function call is the name of the function, followed by more parentheses–for example, sayHello() . By officially calling the function, it tells Javascript to execute the code.
What is a Variable? (5A)
A variable is an identifier for a value. The most common way that variables are used is with the “let” keyword, followed by the name of the variable. An example of this would be: let myText . When the variable has a name, but does not have a value, it is what’s known as declared. It should be given a value, though, so that it serves a purpose. This process is known as initializing the variable. To initialize the variable, you use an equals sign (known as the “assignment” operator) to assign the variable to the contents of the value. For example: let myText = “Good morning!”; . In addition, you should use quotation marks around the contents of the value. Declaring and initializing variables are very important steps in coding, but they also have their differences. Declaring a variable is giving it a name, and initializing it is giving it a value.
The Benefits of RFID (3B)
RFID stands for radio frequency identification. This type of technology is commonly seen on debit/credit cards, and even on Septa key cards. It’s what allows you to tap and pay instead of swiping or inserting the card into the machine. This isn’t the only application for RFID technology though. It’s very useful in the world of supply chain management. A shipping label with an RFID tag has a lot more information than a barcode and can be programmed. In the warehouse, a reader is able to scan the tags from different distances. Passive tags are cheap for the business, but can only be scanned from a few feet away. Active tags have a longer range, but are more pricey. If a business invests in RFID technology, they’ll need to consider this. When we go to the store and tap our card on the machine, we probably save a few seconds compared to inserting or swiping it. However, for a warehouse going through hundreds or maybe thousands of boxes per hour, they would save a substantial amount of time.
ERP vs CRM 3A
ERP, or enterprise resource planning, is a type of software that helps businesses operate more efficiently. ERPs simplify business processes such as supply chain management, procurement, and accounting. ERPs also combine the data from these processes. These systems are often cloud-based, which means that changes to data, or an update to the ERP, will reflect automatically. Any business, big or small, benefits with an ERP because their business will be much more efficient. CRM stands for customer relationship management. These systems are mainly used by those in sales and marketing, but could also be used in HR, accounting, and other areas that are customer-oriented. Where ERPs tend to focus on making and fulfilling orders, CRMs focus on the customer support side of the business. These systems can store customer contact information, email and social media campaigns, and website metrics. For businesses with physical locations, they may want to track customer traffic. Despite these differences, CRMs are similar to ERPs in that they increase efficiency and lower costs.
Threat Modeling 4B
Threat modeling a a type of detective that helps pickup when their are threats being made to a computer software system or infrastructure. Threat modeling is used to pick up any types of threat agents that may be detected virtually. There are many regulation requirements that need to be met with threat modeling such as risk assessment, threat mapping, threat intelligence and even asset identification. As a risk management and Insurance major, this corresponds to what I am studying because risk assessment is critical when it comes to mitigating loss exposures and in this instance, cyber risk is a major risk in itself and also comes with a lot of associated risks. Data protection and cyber security need to be regulated especially since a lot of information from individuals is absorbed through those platforms. Cyber security as well is extremely risky and their are many risks that correspond with cyber. Therefore regulations are placed on the following subjects to help mitigate the risk exposures associated with both aspects. Ransomware is basically when a cyber network is attacked by being hacked, and hospitals tend to become a primary target in this type of risk. This is primarily because hospitals host a multitude of patients that have to turn over personal information such as their medical information, SSN, insurance info and then some which many hackers see as a attribute to their daily lives in helping them hack people’s information. Hospitals become a primary target since the patients have to turn over this personal information before being seen by the doctor or nurses. this makes it easier for attackers to target hospitals since they host such a multitude of potential cyber victims as patients. Some ways to protect yourself online is to just not engage in social media or unfamiliar platforms. Apart from that, one can choose to not engage in cyber activity or using platforms that need to obtain personal information prior to usage. Therefore if I was not born in such a internet evolving generation, I would have been more guarded about my internet usage because I have been a victim of being hacked through the internet whether it was on my social media or on a job seeking platform, both have happened to me and have caused discrepancies in my life.
Digital Platform Pros 4A
There are a lot of pro’s to using digital platforms. Some of the pro’s to using digital platforms are is the advanced technology that is used, apart from the advanced technology is the AI that is typically engraved in the different platforms that are digitized. The network effect is basically a theory where people believe that the more use of a platform or service, the more people will start to use it due to increased value. There are many pros and cons when it comes to cloud computing. Some of the cons include trust because many people find the internet and computer based software untrustworthy, while others believe that there are more adequate ways of computing data part from using the cloud. Some of the pro’s include the cloud being able to keep all the information in one place but additionally, it can be seen as a negative aspect because if the data gets lost in the cloud, then some believe that it cant ever be recovered or it will just be out in the world for anyone to see while they are unable to recover it. The differences between SaaS, PaaS and IaaS are the type of services that it provides to its users. SaaS provides software while IaaS provides Infrastructure and PaaS is the platform which data is based on. API’s is a type of software which allows two parties to effectively communicate with one another. Specifically API’s allows there to be a distinction between two parties while also delivering their messages on both end, therefore creating a transactional method of communication. API’s build value because it connects systems and software to one another while also helping to convert data and strategies. Project managers are managers who are responsible for the planning, monitoring, and execution of a project therefore when it comes to project management, they usually use software and platforms to help monitor the performance, and data being executed and planned out.
Data Protection and Cybersecurity Regulations 4B
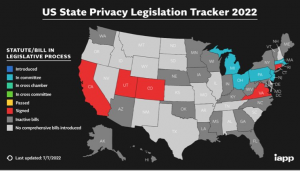
There are so many people in the U.S., and each person has important personal data. In order to keep their information private and secure, there are a few regulations in place. In terms of privacy and personal data, there is the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR). Surprisingly, even though technology is so vast, there aren’t that many federal laws covering cybersecurity. The ones that do exist include the Gramm-Leach-Bliley Act (1999), the 2002 Homeland Security Act, which includes the Federal Information Security Management Act, and the Health Insurance Portability and Accountability Act (HIPAA), created in 1996. There are also some bills being enacted at the state level, but according to the map that we looked at in class, many states do not have regulations established. The states that I do see with signed statutes/bills (indicated in red) are California, Utah, Colorado, Virginia, and Connecticut. For Pennsylvania, it looks like we have something in committee, indicated by the light blue.
The Pros and Cons of Cloud Computing 4A
Cloud computing is the ability to network and store data without the need for a server on-site. Some of the advantages of cloud computing include scalability, collaboration, ease of use, and low costs. One of the reasons why it’s so easy to use is because the businesses using it do not need to worry about tech issues. Any issues that do arise are handled by the cloud company’s IT team. Unfortunately, there are some disadvantages as well. Cloud computing can create concerns with security, data integrity, availability, and pricing. Since the cloud is so big, there’s a higher chance of data breaches. This means a business’s private information could be released. In addition, cloud-computing services are on a pay-as-you-go basis, which means that the more you use, the more you pay. This could technically be a pro and a con, depending on how you look at it. A business that only needs some storage won’t have to pay as much as one that needs a lot more.