Lab 2: Extract Image (Jpeg only)
- Restart Wireshark capture
- Visit google.com
- In the search engine: search for any image (Cars, Sports logos, places, landmarks etc..)
- Visit the site with the image but do not download the image:
- Go Back to wireshark
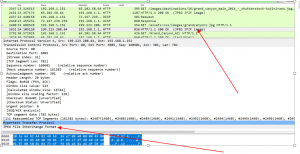
- Identify the traffic pattern of the image search
- Display filter on http
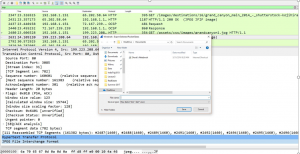
- Based on the available packets identify the http packet with jpeg data
- Note that in the middle pane many other packet numbers are identified which are associated with this JPEG Packet.
- Right Click on JPEG File Interchange Format in the middle pane
- Upon right clicking – select export packet bytes. It will look similar to image below. Provide a file name. And ensure that the file type is JPEG (extension). And under save as type – select ALL.
Find the file that you saved (jpg) upon opening you would have identified the image you visited.
Using the PCAP (wiresharklab.pcapng) provided, identify extract the image and submit it with the LAB submissions.
- Identify the IP address of the bank visited
- Extract the “cars” jpeg within the packet capture.