Posts
Importance of ERD
-
An ERD (Entity-Relationship Diagram) is a graphical representation of entities and their relationships to each other in a database. It’s used to model the database structure and ensure that all necessary data is included.
-
The two notations for ERDs are Chen notation and Crow’s Foot notation.
-
The primary symbols in an ERD are:
- Entity: A person, place, thing, concept, or event that can be uniquely identified and represented in the database.
- Attribute: A characteristic or property of an entity.
- Relationship: A connection between two or more entities that describes how they’re related.
- In Crow’s Foot notation, there are four types of relationships:
- One-to-One (1:1): Each entity in the relationship can have only one related entity.
- One-to-Many (1:M): One entity in the relationship can have multiple related entities, but the related entities can have only one entity.
- Many-to-One (M:1): Multiple entities in the relationship can be related to a single entity.
- Many-to-Many (M:M): Multiple entities in the relationship can be related to multiple entities.
These relationships are expressed by drawing lines between the entities, with different line types and symbols used to indicate the relationship type.
- In an ERD table, key things include:
- Entity names and their attributes.
-
Salesforce is a cloud-based customer relationship management (CRM) software that helps businesses manage their customer interactions, sales, and marketing activities.
-
Dynamic Dashboards in Salesforce are interactive dashboards that allow users to filter and drill down into data in real-time. Their functions include providing real-time data insights, tracking key performance indicators, and identifying trends and patterns.
-
There are three types of cardinality in ERDs:
- One-to-One (1:1)
- One-to-Many (1:M)
- Many-to-Many (M:M)
Cardinality is utilized to define the relationship between entities and indicates how many instances of one entity can be associated with another entity. It’s typically represented using symbols and notation in ERDs, such as the crow’s foot notation.
SalesForce and Databases
Salesforce is a popular customer relationship management (CRM) platform that allows businesses to manage their customer interactions and streamline their sales processes. It is widely used in many industries, including finance, healthcare, and retail. Learning Salesforce can be valuable for individuals and organizations because it provides a powerful set of tools to manage and analyze customer data, automate business processes, and improve communication and collaboration within a team.
Creating a database in Salesforce can have several benefits, including:
- Centralized data management: Salesforce provides a single location to store all customer data, making it easy to access and manage customer information from one place.
-
Improved data accuracy: By using Salesforce’s validation rules and data cleaning tools, you can ensure that your data is accurate and up-to-date, reducing errors and improving overall data quality
In swim lane diagrams, the symbols used and their meanings are:
-
Circle: Used to indicate the start and end points of a process or activity.
-
Rectangle: Used to represent a task or activity.
-
Diamond: Used to represent a decision point in the process flow, where different paths or options are available.
-
Arrow: Used to show the direction of the process flow.
-
Cylinder: Used to represent a data store or database.
The benefits of swim lanes include:
-
Clarity: Swim lane diagrams provide a clear, visual representation of a process or workflow, making it easy to understand and communicate.
-
Accountability: By assigning tasks and activities to specific individuals or teams within a swim lane, it becomes clear who is responsible for each step of the process.
6a Question
The if/else statement executes a block of code if a specified condition is true. If the condition is false, another block of code can be executed. The if/else statement is a part of JavaScript’s “Conditional” Statements, which are used to perform different actions based on different conditions. The general form of if-else is as follows: if (test-expression) { True block of statements } Else { False block of statements } Statements; n this type of a construct, if the value of test-expression is true, then the true block of statements will be executed. The isNaN() function determines whether a value is NaN when converted to a number Because coercion inside the isNaN() function can be surprising, one may alternatively want to use Number.isNaN().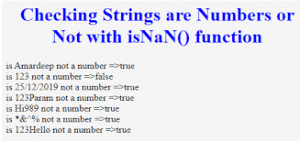
7a Question
HTML (the Hypertext Markup Language) and CSS (Cascading Style Sheets) are two of the core technologies for building Web pages. HTML provides the structure of the page, CSS the (visual and aural) layout, for a variety of devices. JavaScript is a lightweight, interpreted scripting language widely used to enhance and add content to a web page. CSS is the language for describing the presentation of Web pages, including colors, layout, and fonts. It allows for it to adapt the presentation to different types of devices, such as large screens, small screens, or printers. CSS is independent of HTML and can be used with any XML-based markup language. JavaScript in the browser can interact with HTML elements, which are event emitters, that is, subjects able to emit events. Without JavaScript the button is inanimate
5b Question
A function in JavaScript is a set of statements that performs a task or calculates a value, but for a procedure to qualify as a function, it should take some input and return an output where there is some obvious relationship between the input and the output. JavaScript has five functions built into the language. They are eval, parseInt, parseFloat, escape, and unescape. When you define a function you give a name to a set of actions you want the computer to perform. When you call a function you are telling the computer to run (or execute) that set of actions. Functions are data, and therefore can be passed around just like other values. This means a function can be passed to another function as an argument. This allows the function being called to use the function argument to carry out its action.
5a Question
At first I was intimated going into this week I had never worked with coding or javascript prior but I can say it hasn’t been as rough as expected. A JavaScript variable is simply the name of a storage location. There are two types of variables in JavaScript local variable and global variable. There are some rules while declaring a JavaScript variable (also known as identifiers). Name must start with a letter (a to z or A to Z), underscore, or dollar sign. In JavaScript, we can use either var or let keyword to declare variables. For example, var x; let y; Here, x and y are variables. Arithmetic operators in JavaScript, and what they all do are + it adds, – it subtracts, * it multiples, / it divides but this result is a floating-point number, % it divides but this result gives the remainder. The order they are in also matters.
4b Questions
Threat modeling is a process by which potential threats, such as structural vulnerabilities or the absence of appropriate safeguards, can be identified and enumerated, and countermeasures prioritized. A cybersecurity regulation comprises directives that safeguard information technology and computer systems with the purpose of forcing companies and organizations to protect their systems and information from cyberattacks like viruses, worms, Trojan horses, and phishing. Some regulations involved with data protection and cyber security conclude that businesses must comply with various laws on cyber security, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the California Consumer Privacy Act (CCPA). Failure to comply with these laws can result in significant fines and penalties.

Loops
Hello class,
Loops are very important when it comes to coding. Loops makes programing easy because the same code can run over and over again with different values every time. There are many types of loops. In class, we learned about “for” loops which run codes as many times as a condition is true. We also learned about “while” loops which will run codes while certain conditions are true. It is very important to remember that sometimes we need to initiate values before these loops are executed. Finally, loops have to have a final expression which will be executed if all other conditions failed. We can also specify the number of times loops can run.
4a Question
Some pros of using digital platforms are improved efficiency and automation of processes, enhanced user experience and customization options, increased data collection and analysis capabilities, lower costs and scalability compared to traditional solutions.The network effect refers to the concept that the value of a product or service increases when the number of people who use that product or service increases. Some examples are Rideshare: Uber, Lyft. Delivery: Grubhub, DoorDash, Uber Eats, Instacart, Postmates. Social Media: Facebook, Twitter, Instagram, LinkedIn, Snapchat, Pinterest. Some pros of cloud computing included cost savings and increased efficiency, scalability and flexible resource allocation, access to advanced technology and tools, improved disaster recovery and data security. While cons of cloud computing included but are not limited to dependence on internet connectivity, potential for vendor lock-in, security and privacy concerns, complexity of managing and integrating multiple cloud services.
My digital identity refers to the online presence and representation of an individual. This includes information such as personal details, social media profiles, online activity, and interactions with others. To manage their digital identity, individuals can use privacy settings, be mindful of the information they share online, and actively monitor and maintain their online presence.
Having a good digital identity is important because it can impact a person’s personal and professional life. It can affect how people perceive them, their reputation, and even their job prospects. It is also important because it can protect individuals from identity theft and online fraud.
The Management Information Systems (MIS) community platform is a place where individuals and organizations can connect, share information and best practices, and collaborate on projects related to the field of management information systems.
The purpose of building an e-portfolio is to showcase an individual’s work, skills, and achievements in a digital format. It can be used as a tool for self-reflection, professional development, and to demonstrate one’s capabilities to potential employers or clients. It can include a variety of items such as resume, work samples, and testimonials.