https://medium.freecodecamp.org/lets-enhance-how-we-found-rogerkver-s-1000-wallet-obfuscated-private-key-8514e74a5433
This article is a demonstration of why you should always be very careful when sharing any information publicly. The authors of this article detailed a process of image correction and QR code “hacking” to figure out information on Roger Ver’s bitcoin wallet that was displayed during an interview he gave on a French TV show. Through the use of some very clever thinking and software work, they were able to figure out Roger’s private key. The victim, Roger Ver, actually put this information up knowingly and offered the wallet to anyone who could figure it out. Even so, it is a difficult process, as the authors detail the steps:
- Information gathering
- Let’s enhance! Image Analysis
- QR code standard part 1
- QR code reconstruction
- QR code standard part 2
- QR code decoding
- Error Correction Code
- Python & Brute force
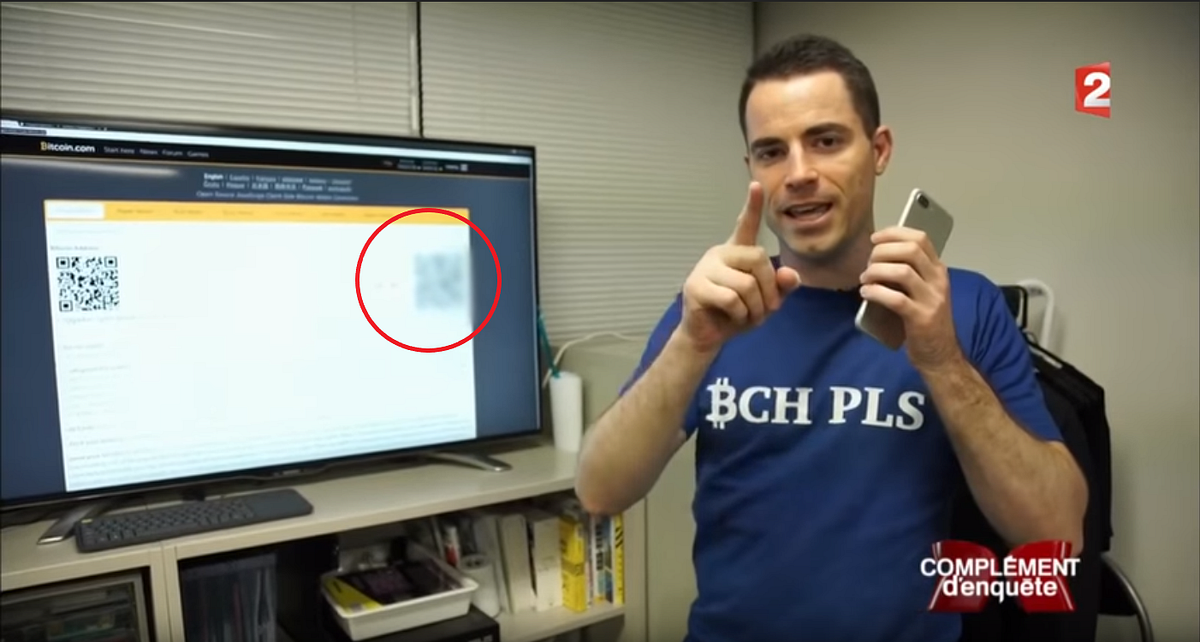
Check it out!