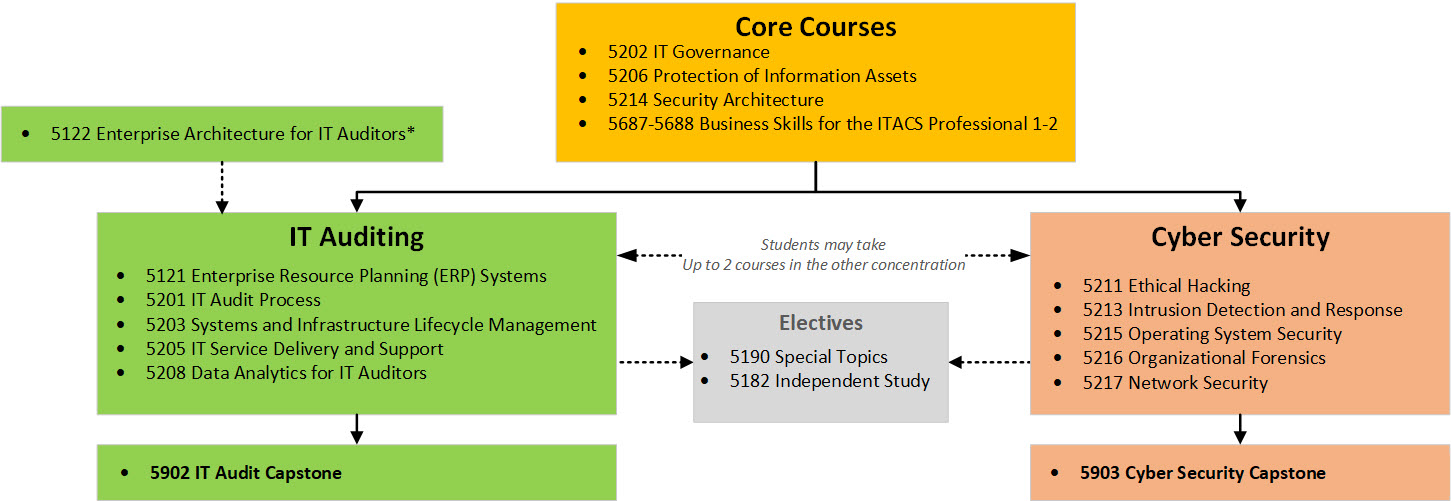
Organization of courses
ITACS Program courses are organized in Core, IT Audit and Cyber Security groups. Five core courses are mandatory for students of both IT Audit and Cyber Security concentrations. Beyond the core courses, there are 6 IT Audit concentration courses and 6 Cyber Security concentration courses. Students lacking technical knowledge of computers and information technology will be required to take an additional remedial education course: MIS 5122 Enterprise Architecture for IT Auditors. All ITACS courses are Management Information System (MIS) department courses, organized as illustrated in the figure below:
For ITACS courses and their descriptions click here this will take you to the Temple University Bulletin’s ITACS Program Requirements web page. For a course’s description, click on the course number (e.g. MIS 5202).