-
Shahla Raei posted a new activity comment 7 years, 9 months ago
Paul Thank you so much for sharing this information it was helpful and I added my screen shot in to media section of our blog. here is the link to it .
http://community.mis.temple.edu/mis520817/files/2017/02/Table-script.png
I have experience working with Microsoft SQL and PLSQL Developer, and this information will help me to love working…[Read more]
-
Shahla Raei wrote a new post on the site MIS5208 Spring 2017 7 years, 9 months ago
This article is talking about audit management solutions and how the security and risk management leaders can improve productivity and manage the internal auditor’s role by facilitating audit management s […]
-
Shahla Raei posted a new activity comment 7 years, 9 months ago
Blake,
Very Interesting topic, and as Sean mentioned to a good point that the trend of data analytics that being outsourced is growing.
I believe If the data is critical to the company’s business survival, it should be kept in-house. Other analytics can be outsourced.I found a related example about your topic online:
Example is r…[Read more]
-
Shahla Raei posted a new activity comment 7 years, 9 months ago
Nice topic, Unethical behavioral!
Based on my research, Financial regulation cannot prevent this kind of scandal. Finally it is human nature at the root of this problem. In this case I’ve found out that Wells Fargo had a two-day ethics workshop in 2014 explicitly telling their employees not to create fake customer accounts. However, the…[Read more] -
Shahla Raei posted a new activity comment 7 years, 9 months ago
Wenlin,
Interesting topic, Use of AI is not a new concept. AI solutions can be used to improve security across a number of business in financial industries. Organizations rely on AI to trace steps by analyzing the behaviors of transactions and devices. Based on my research I found an article released on December 2016, stating that master card…[Read more]
-
Shahla Raei wrote a new post on the site MIS5208 Spring 2017 7 years, 9 months ago
Based on our last week topic I found this website interesting.
The ACFE (Association of certified fraud examiners). The ACEF is the world’s largest anti-Fraud organization. And providing anti-fraud training t […]
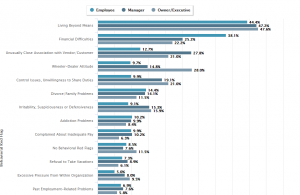
-
Very interesting site for sure. Some of the items listed under the ‘initial detection of occupational fraud’ tab reminds me of a situation my wife encountered. My wife worked for a large credit union; she was the regional manager for the state of New Jersey. One of her branches had an issue which required an immediate audit of the branch. From what I remember, the initial error was not major infraction, however the management was bound by policy and procedures to conduct an internal audit of the branch. Well, during the audit, the regional manager (my wife) discovered that controls were being ignored and procedures were being bypassed. And as luck would have it, the audit uncovered a major act of fraud (attempted on the very day of the impromptu audit!). A teller falsified a ledger from the cash vault and attempted to steal $5000 in $20 bills. In all likelihood, the theft would have been discovered at a later time. However, due to violations in procedures, finding out who committed the fraud and how the theft occurred would have been more challenging then it had to be. Ultimately, surveillance cameras revealed one suspicious movement of the guilty teller which led to the stashed $5,000.
So, as indicated on the ‘detection’ tab of the website you posted, internal audits can and do lead to exposing fraud.
-
-
Shahla Raei wrote a new post on the site MIS5208 Spring 2017 7 years, 9 months ago
My name is Shahla Raei and I am currently an Internal IT Auditor Intern at Chubb. I am part time student, and will be graduating on June 2017. I am originally from Tehran, Iran. I majored in Computer Software […]
-
Shahla Raei posted a new activity comment 8 years ago
Online Ad Industry Threatened by Security Issues
In this article mentioned nowadays Cybercriminals are looking for powerful alternatives and now targeting ad industries.
The online advertising industry is at an inflection point, also ad blockers and potential regulation are considering a risk. It’s facing a big security problem, and associated…[Read more] -
Shahla Raei posted a new activity comment 8 years ago
Yang,
Correct, I wanted to mention to this week assignment and submitting our presentation. our team come up a solution to help company identify their sensitive information. one of the document we ask them to prepare it for the future meeting was organizational chart. I think this chart is an important chart in an organization and help auditor…[Read more]
-
Shahla Raei posted a new activity comment 8 years ago
Neil,
Its is really an interesting point , and privacy is an important concept, specifically in 21st century, Now a days has become the century of Big Data and Information Technology allows for the storage and processing of big data. so testing the Privacy effectiveness is always matter.
-
Shahla Raei posted a new activity comment 8 years ago
Right, Access management dealing with authorization and authentication. I liked your example. as you mentioned knowing the distinction between these two helps the stakeholders in understanding how their interests are protected and implemented by Identity and Access Management technologies
-
Shahla Raei posted a new activity comment 8 years ago
Mansi,
Good point, I agree with you it totally depends on nature of business, However outbound traffic is more important in my view, I remember in advisory session we had couple weeks ago, we analyze the case that the problem was in outbound traffic wasn’t protected so there was a main problem on that case.
-
Shahla Raei posted a new activity comment 8 years ago
Fred,
I think it might be depends on nature of business, if the organization doesn’t want to communicate in industry so blocking all income network is good practice, However, I think in terms of confidentiality we should block or be sensitive about outbound information.
-
Shahla Raei posted a new activity comment 8 years ago
Loi,
Its an interesting article its explains the detail of DDos attack, also its point out the rationalization of attacker.
-
Shahla Raei posted a new activity comment 8 years ago
On October 21st I got email from Big interview website, which I am a member of it. That the global Internet Outages Affecting their website. I was curious about the breach and did search about it.
On October 21st , ton of websites and services, including Spotify and Twitter, were unreachable because of a distributed denial of service (DDoS)…[Read more]
-
Shahla Raei posted a new activity comment 8 years ago
Noah,
Its interesting, I didn’t think the way you explained! True its based on reason for attacks or what is the goal of attackers.
If attacker aims botnet, spam phishing as it sent out in mass quantities can be a bigger treat, and if attacker aims specific information spear phishing as its target specific group of organization is a bigger treat.
-
Shahla Raei posted a new activity comment 8 years ago
Spear phishing is highly specialized attacks against a specific target or group of targets to collect information or gain access to systems through personalized e-mail messages and social engineering. This is not random kind of attack, attacker knows target name, target email address, and at least a little about target. It’s a more in depth…[Read more]
-
Shahla Raei posted a new activity comment 8 years, 1 month ago
Customer trust is often damaged after a data breach. following Yahoo recent disclosure of a data breach that affected more than 500 million accounts. Verizon may demand to renegotiate its $4.8 billion deal for Yahoo Inc. It’s yahoo’s responsibility to prove the full of impact and Verizon could allow it to change the terms of the takeover.
T…[Read more] -
Shahla Raei posted a new activity comment 8 years, 1 month ago
They are different!
Disaster recovery plan provides detailed strategies about processes and procedures an organization must put in place immediately to ensure that critical functions can continue during and after a disaster to recover from the event. Such as emergency supplies, flashlights, backup business information.
Business Continuity…[Read more]
-
Shahla Raei posted a new activity comment 8 years, 1 month ago
Fred,
As you mentioned , PHYSBITS focuses on the human aspect of physical security by integrating information security. I agree with Ex- employee risk and the controls you considered for it is smart , adding additional level of access control.
- Load More
Connect and innovate with an elite information systems program
Footer
MANAGEMENT INFORMATION SYSTEMS
Fox School of Business
Temple University
210 Speakman Hall
1810 N. 13th Street
Philadelphia, PA 19122
