-
Vaibhav Shukla posted a new activity comment 7 years, 12 months ago
The main problem I felt that why the auditing of logs for data being transferred is done in 2 years.This process should have been done more frequently.If this auditing was done in 6 months there was chances of tracking the person more fast.Its hard to figure out whether the data was not or will not be used for any malpractice.
-
Vaibhav Shukla posted a new activity comment 7 years, 12 months ago
Yeah and I firmly believe that snowden leaks were like the turning point in face of IT Security.A lot of countries and organizations changed their strategies to secure their information systems .Storing data locally will have a more control on the flow of data .National Security is absolutely important and countries can make laws pertaining to it
-
Vaibhav Shukla posted a new activity comment 8 years ago
Lost thumb drives bedevil U.S. banking agency
A U.S. banking regulator says an employee downloaded a large amount of data from its computer system a week before he retired and is now unable to locate the thumb drives he stored it on.
The Office of the Comptroller of the Currency, which is a part of the Department of the Treasury, said the loss…[Read more] -
Vaibhav Shukla posted a new activity comment 8 years ago
Yeah even I had a initial feeling that what can be the sensitive information w.r.t the blood donors as they can have just information of blood donation history and name of donor.
But I felt this is a serious breach when the secret private questions like ” engaged in “at-risk” sexual behavior” and blood type is revealed in public.
Blood don…[Read more] -
Vaibhav Shukla wrote a new post on the site ITACS 5211: Introduction to Ethical Hacking 8 years ago
Vladimir Putin’s government is threatening to shut down business networking site LinkedIn. The threat stems from a recent law in Russia that requires all companies doing business in the country to store their d […]
-
Vaibhav Shukla posted a new activity comment 8 years ago
It is very important to know the difference between the identity and access management as we have to clarify the basic question ” When the user identity is established can he access the service? ”
Answer is No . Authentication is not equal to Authorization .After authentication there needs to be an access control decision. The decision is based…[Read more] -
Vaibhav Shukla wrote a new post on the site ITACS 5211: Introduction to Ethical Hacking 8 years ago
Scanning Exercise
Video
scanning-ppt
summary-pdf
-
Vaibhav Shukla commented on the post, Dirty COW, on the site 8 years ago
The article clearly throws light on how this vulnerability is a serious threat and way to fix it by patching our operating systems.But there are million of devices which cannot be patched which remains a serious concern.
Many gadgets using linux doesnt support patching and can be security rsik -
Vaibhav Shukla commented on the post, 7 Best Social Engineering Attacks Ever, on the site 8 years ago
I really like the RSA SecurID Breach .Usually people tell its gullible people tricked into social engineering but there are also employees working in security company getting tricked .It is expected from employees of such company to be aware of such social engineering tricks.This also reveals how can the zero day attacks could be a lot dangerous
-
Vaibhav Shukla commented on the post, Create Your Own MD5 Collision, on the site 8 years ago
The article is great and I feel the hash collision can also be created if we convert the hex code into the binary code.
The main vulnerability exploited in MD5 collision is the length extension because of this length-extension behavior, we can append any suffix to both messages and know that the longer messages will also collide. -
Vaibhav Shukla posted a new activity comment 8 years ago
Inorder to determine network capacity is adequate or inadequate we need to have a network capacity planning which includes finding out
1) Traffic Characteristics-Type and amount of traffic
• Traffic volumes and rates
• Prime versus non-prime traffic rates
• Traffic volumes by technology2) Present Operational Capacity
• WAN percent…[Read more] -
Vaibhav Shukla posted a new activity comment 8 years ago
Millions of Indian debit cards ‘compromised’ in security breach
On Wednesday, India’s largest bank, State Bank of India, said it had blocked close to 600 thousands debit cards following a malware-related security breach in a non-SBI ATM network. Several other banks, such as Axis Bank, HDFC Bank and ICICI Bank, too have admitted being hit by s…[Read more]
-
Vaibhav Shukla wrote a new post on the site ITACS 5211: Introduction to Ethical Hacking 8 years ago
Major websites were inaccessible to people across wide swaths of the United States on Friday after a company that manages crucial parts of the internet’s infrastructure said it was under attack.
Users reported s […]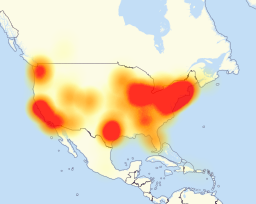
-
Vaibhav Shukla posted a new activity comment 8 years ago
A Distributed Denial of Service (DDoS) attack is an attempt to make an online service unavailable by bombarding it with traffic from multiple sources
Spear-phishing attack is carefully crafted and customized to look as if it comes from a trusted sender on a connected subject. Spear-phishing scams often take advantage of a variety of methods to…[Read more] -
Vaibhav Shukla commented on the post, Weekly Question #8: Complete by November 2, 2017, on the site 8 years ago
I think its a very bad approach by a government agency in maintaining its IT infrastructure.
The IT systems were like full of vulnerabilities and the officials were waiting for such data breach event to take place in-order to put everything on track .
The common items mentioned in it are like some of the key in maintaining IT security in an…[Read more] -
Vaibhav Shukla commented on the post, Weekly Question #8: Complete by November 2, 2017, on the site 8 years ago
Yeah but I still feel recognizing the cyber security hacks as national security challenge is very important.
This actually proves that information security is gaining importance in coming times that it even needs to be a part of political strategy for the competitors and I think in coming time this could be a very important factor to be seen in…[Read more] -
Vaibhav Shukla wrote a new post on the site ITACS 5211: Introduction to Ethical Hacking 8 years ago
A dangerous banking Trojan, named Acecard, asks android users to send a selfie holding their ID card.This threat tricks users into installing the malware by pretending to be an adult video app or a codec/plug-in […]
-
Interesting article Vaibhav. Very scary, and hopefully people aren’t gullible enough to send a selfie of their ID card, especially if its related to an adult video app..I’m sorry, but if you get tricked into doing this, then its your fault.
-
Perfect example of social engineering at its best. Sit back and let the end users feed you all the information you need without a care in the world.
-
Wow. Thanks for sharing Vaibhav. This is a very low-tech scheme that could cause a lot of trouble for users that think this is just a new security feature. I can see a lot of folks falling for this type of scam and how it can create a lot of hassle for them. There is such a strong need for cyber awareness and education to the general public.
-
-
Vaibhav Shukla posted a new activity comment 8 years ago
Quantum computing in simple words is something that allows a particle to be both a zero and a one at the same time. Quantum cryptology depends on physics, not mathematics.
Quantum cryptography uses photons to transmit a key. Once the key is transmitted, coding and encoding using the normal secret-key method can take place.
But question comes…[Read more] -
Vaibhav Shukla posted a new activity comment 8 years ago
How is NSA breaking so much crypto?
The Snowden documents shows that NSA has built extensive infrastructure to intercept and decrypt VPN traffic and suggest that the agency can decrypt at least some HTTPS and SSH connections on demand.
However, the documents do not explain how these breakthroughs work.If a client and server are speaking…[Read more] -
Vaibhav Shukla posted a new activity comment 8 years ago
BCP is a plan that allows a business to plan in advance what it needs to do to ensure that its key products and services continue to be delivered in case of a disaster,.A business continuity plan enables critical services or products to be continually delivered to clients. Instead of focusing on resuming to a complete strength after a disaster, a…[Read more]
- Load More
Connect and innovate with an elite information systems program
Footer
MANAGEMENT INFORMATION SYSTEMS
Fox School of Business
Temple University
210 Speakman Hall
1810 N. 13th Street
Philadelphia, PA 19122
