-
Shenika Balfour and
 Jeta Gjana are now friends 8 years, 2 months ago
Jeta Gjana are now friends 8 years, 2 months ago -
Thomas Forte and
 Jeta Gjana are now friends 8 years, 6 months ago
Jeta Gjana are now friends 8 years, 6 months ago -
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 7 months ago
Hey guys,
Some of you might already know this but for those who have not been notified yet, you can attend 4 online courses and become Splunk certified for free 🙂
Check it out!
-
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 7 months ago
“Ransomware, hospital hacking present growing cybersecurity threats”
Hackers crippled computer systems at a major hospital chain, MedStar Health Inc., one of the the largest health care providers in the Bal […]
-
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 7 months ago
Assigned Reading:
Aircrack-ng Suite should be used in a Linux environment and not in a Windows OS since there is not much support for it. For someone who has not been previously exposed to this tool, the […]
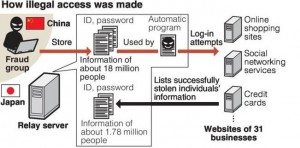
-
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 7 months ago
Assigned Readings:
The Institute of Electrical and Electronics Engineers (IEEE) 802.11 is a set of media access control and physical layer for providing connectivity between wireless technology and wired […]
-
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 7 months ago
“Hacker’s Typo Tipped Off Authorities on Billion-Dollar Heist”
A spelling mistake in an online bank transfer instruction helped prevent a nearly $1 billion heist last month involving the Bangladesh central bank […] -
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 8 months ago
Since there’s no assigned readings (according to the syllabus), I thought I would share this interesting article: “Office puts chips under staff’s skin”.
Epicenter, a new hi-tech office block in Sweden, are tr […]
-
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 8 months ago
Assigned readings:
Burp Suite is a tool that allows security testing of Web applications. This framework is very powerful for if it is used properly, it identifies vulnerabilities and exploits them. This tool […]
-
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 8 months ago
“Keybase Releases Encrypted File-Sharin iPhone App”
Keybase last week announced the alpha release of the Keybase app for the iPhone with a cryptographically secure file mount. Users can write data in an […]
-
Jeta Gjana posted a new activity comment 8 years, 9 months ago
Week 4 Takeaways
CISA
Every company relies on IT to complete its project. Some of the areas that IT aid the process include development, acquiring, integrating, and maintaining application systems that are critical to the company. The SDLC is the process which every company relies on and it works great if one uses at its best capabilities.…[Read more] -
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 9 months ago
Assigned readings:
Metasploit extended usage includes various capabilities, such as Mimikatz, a user friendly metepreter script composed of various tasks that attackers will want to perform on the initial […]
-
Jeta Gjana posted a new activity comment 8 years, 9 months ago
Week 3 Takeaways
CISA Review:
3.5.4 – Risk associated with software development
There exist various risks with designing and developing a software, ranging from business risk to project risk. Business risk occurs when the new system may not meet the user’s requirements. On the other hand, project risk occurs when the financial budget is lim…[Read more] -
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 9 months ago
Assigned readings:
Metasploit Unleashed allows various functions, such as the abilities to conduct MSF Post Exploitation,
Meterpreter Scripting, and Maintaining Access. MSF Post Exploitation allows the user to […] -
Jeta Gjana posted a new activity comment 8 years, 9 months ago
Week 2 Takeaways:
CISA Review
· 3.3: Project Management StructureThere exist many factors why a project is considered a success or worst, a failure. Some of these attributes include a general approach, the detail workflow of documentation, system view, etc. Therefore, there now exist a number of standards and organization who…[Read more]
-
Jeta Gjana posted a new activity comment 8 years, 9 months ago
Week 1 Takeaways
CISA Review
· 3.2: Benefits RealizationThis section deals with the major factors of a project, such as cost, quality, delivery date, reliability, and dependability. These factors are further analyzed to see which weaknesses or strengths complete and maintain the system. The function of an IS Auditor is to…[Read more]
-
Jeta Gjana wrote a new post on the site Advanced Penetration Testing 8 years, 9 months ago
Assigned readings:
The Metasploit Unleashed (MSFU) is an open source penetration tool. This ethical training course also has the objective to provide security awareness for the underprivileged children in East […]
-
Jeta Gjana wrote a new post on the site Introduction to Ethical Hacking 8 years, 11 months ago
Reading Summary: Evasion
Organizations mostly use firewalls and Intrusion Prevention System (IPS) to protect its network infrastructure. IPS is as an evasion technique used to detect any security attacks. […]
-
Jeta Gjana wrote a new post on the site Introduction to Ethical Hacking 8 years, 11 months ago
Reading Summary: Web Services
Web services is a tactic used to improve productivity in terms of increasing the speed and quality of information flow, as well as to make it easier for producers and consumers of […]
-
Jeta Gjana wrote a new post on the site Introduction to Ethical Hacking 9 years ago
Reading Summary: SQL Injection
SQL injection is one of the most common vulnerabilities in web applications and that is why it is very crucial to test for vulnerabilities when one creates a website since it […]
- Load More
Connect and innovate with an elite information systems program
Footer
MANAGEMENT INFORMATION SYSTEMS
Fox School of Business
Temple University
210 Speakman Hall
1810 N. 13th Street
Philadelphia, PA 19122
