-
Wenhang Lu wrote a new post on the site MIS 5213 Summer 2016 8 years, 8 months ago
Hi guys,
I finally got my snort working. We have to use the Registered version of snort rules from Snort website. If you are using latest version of Snort then you will need to download […]
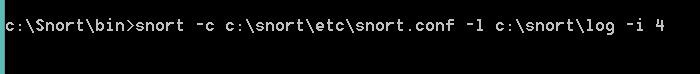
-
Wenhang Lu posted a new activity comment 8 years, 9 months ago
Hi there! My name is Wen Lu. I am a part-time graduate student. I will be graduating this July. I received my undergraduate degree in Information Science & Technology from Temple University. I’m currently working at Computer Services Help Desk at Temple University. See y’all on Monday.
-
Wenhang Lu posted a new activity comment 9 years, 5 months ago
On the page 2 of week 1 presentation slides, your email address should be ” . edu “
-
Wenhang Lu commented on the post, Week 10 Perimeter Security Lecture Notes Posted, on the site 9 years, 9 months ago
Thank you for posting the slides!
-
Wenhang Lu commented on the post, ICE 5.1 Telling a Story through Visualization, on the site 9 years, 10 months ago
When you get a chance, could you post the week 10 Powerpoint slides. Thanks!
-
Wenhang Lu commented on the post, Progress Report for Week Ending, September 29, on the site 10 years ago
Hello everyone, check out this website that let you draw professional-quality diagrams in your browser. Link: https://www.gliffy.com
-
Wenhang Lu commented on the post, Questions for the TJX case study, on the site 10 years, 2 months ago
If anyone needs help finding a copy of the TJX case let me know by replying to this comment.
-
Wenhang Lu commented on the post, Week 12 Materials Posted, on the site 10 years, 2 months ago
According to a CyberArk report, the exploitation of privileged accounts occurs in almost every targeted attack. The primary reason why attacks are so hard to detect and stop because hackers are using privileged accounts. The report states privileged accounts enable attackers to have unrestricted access and ability to cover their tracks and…[Read more]
-
Wenhang Lu commented on the post, Week 11 Materials Posted, on the site 10 years, 2 months ago
According to Kaspersky Lab, over the last four years malicious hackers have been using so-called the “DarkHotel” trick to steal data from company executives while they staying at luxury hotels in Asia. The hackers wait for victims to connect to the compromised hotel Wi-Fi network then trick them into downloading and installing a backdoor that…[Read more]
-
Wenhang Lu commented on the post, Progress Report for Week Ending, March 22, on the site 10 years, 2 months ago
Researchers at Palo Alto Networks Company discovered a malware called WireLurker targeting users in China. The WireLurker has been infecting both iOS and Mac OS systems. According to Palo Alto Networks, 467 infected applications were downloaded over 356,104 times in the past six months. WireLurker can collect information from iOS devices like…[Read more]
-
Wenhang Lu commented on the post, Week 9 Materials Posted, on the site 10 years, 3 months ago
Following are the readings for this week’s Network Security topic if you are using Vacca’s 2nd edition book.
2012, Vacca 2nd Edition:
===================Chapter 5 Guarding Against Network Intrusions
Chapter 9 Unix and Linux Security
Chapter 10 Eliminating the Security Weakness of Linux and Unix Operating Systems
Chapter 11 Internet…[Read more] -
Wenhang Lu commented on the post, Week 8 Materials Posted, on the site 10 years, 3 months ago
Google launches two-step verification service that is based on a physical USB key (Security Key). Google is offering the Security key feature on all Google Account sites free but user needs to buy a compatible USB device from a U2F participating vendor. Currently, It only works with Chrome browser but security key will work everywhere FIDO U2F is…[Read more]
-
Wenhang Lu commented on the post, Progress Report for Week Ending, February 9, on the site 10 years, 3 months ago
The Dropbox was reported “hacked” on Monday as an unknown individual posted hundreds of login credentials for Dropbox on a site called Pastebin. The article stated that the hacker has over 7 million Dropbox users’ username and password, and will release them in return for Bitcoin donations. Dropbox however stated that they were not hacked and…[Read more]
-
Wenhang Lu commented on the post, Happy Birthday SNL // the typists from the Carol Burnett show, on the site 10 years, 3 months ago
A new ATM malware called Tyupkin was found on more than 50 ATM machines in Eastern Europe. The malware is designed to work on ATMs running 32-bit version of Windows. Criminals behind the attacks only infected ATMs without alarms installed. To infect the ATM, attackers have to gain physical access to ATM, and then insert a bootable CD to install…[Read more]
-
Wenhang Lu commented on the post, Happy Birthday SNL // the typists from the Carol Burnett show, on the site 10 years, 4 months ago
My news article is about the new security vulnerability known as the Bash bug. This bug was discovered yesterday. The vulnerability affects versions 1.14 through 4.3, or in other words, about 25 years’ worth of Bash versions. Bash is an interpreter that allows you to orchestrate commands on Unix and Linux systems. It is like the command prompt on…[Read more]
-
Wenhang Lu commented on the post, Happy Birthday SNL // the typists from the Carol Burnett show, on the site 10 years, 4 months ago
2009, Vacca 1st Edition:
==================
Chapter 16: Information Technology Security Management2012, Vacca 2nd Edition:
==================
Chapter 24: Information Technology Security Management -
Wenhang Lu commented on the post, Happy Birthday SNL // the typists from the Carol Burnett show, on the site 10 years, 4 months ago
Key point:
The responsibility for identifying a suitable scale for threat valuation, asset valuation, and vulnerability valuation lies with the organization.Question:
What is the best way to handle residual risks after risk treatment? -
Wenhang Lu commented on the post, Week 4 Materials Posted, on the site 10 years, 4 months ago
My article is about the Chinese Academy of Science will launch a face recognition payment app next year. The face recognition system can pick faces from a crowd with 99.8 percent accuracy from 91 angles. Once the users install the app on their mobile devices and link it with bank accounts or credit cards, it will take “one second” for the system…[Read more]
-
Wenhang Lu commented on the post, Week 4 Materials Posted, on the site 10 years, 4 months ago
Hi folks,
I think professor Senko posted the wrong chapters. This week’s readings should be:
– 2009 Vacca 1st Edition:
==================
Chapter 15 – Security Management Systems
Chapter 35 – Risk Management– 2012 Vacca 2nd Edition:
==================
Chapter 22 – Security Management Systems
Chapter 53 Risk Management -
Wenhang Lu commented on the post, Week 3 Materials Posted, on the site 10 years, 4 months ago
Readings – Key Point:
During risk analysis, a security control is put in place if it is cost effective relative to the exposure of the organization. Security policies are the least expensive means of the control and often the most difficult to implement.
- Load More
Connect and innovate with an elite information systems program
Footer
MANAGEMENT INFORMATION SYSTEMS
Fox School of Business
Temple University
210 Speakman Hall
1810 N. 13th Street
Philadelphia, PA 19122
