Monthly Archives: March 2016
Week 13 recent Cyber Security News…
In the Cyber Security News lately…
www.ehackingnews.com/2015/11/malware-detected-in-martels-cameras.html
“iPower Technologies, a U.S security company and network integrator, has discovered a copies of Conficker malware in the Martel Frontline Camera with GPS, one of the largest manufacturers of police in-car video systems in America, whose product is being sold and marketed as a body camera for official police department. When the camera was connected to a computer, iPower’s antivirus software immediately caught the virus and quarantined it. However, if the computer did not have antivirus actively protecting the computer it would automatically run and start propagating itself through the network and Internet, iPower said in a post. In the iPower virtual lab environment, packet captures were also run on the infected PC to view the viruses’ network activity using Wireshark. The virus, classified as a worm virus, immediately started to attempt to spread to other machines on the iPower lab network, and also attempted several phone home calls to Internet sites.”
Presentation and Video Link
Advanced Penetration Testing -Week-12
You have been invited to attend a Mediasite presentation.
Presentation Details:
Title: =MIS 5212.001_3/28/2016
Date: Monday, March 28, 2016
Time: 5:30 PM (UTC-05:00) Eastern Time (US & Canada)
Duration: 2:30:00
Link: http://tucapture.fox.temple.edu/Mediasite/Play/ab016798f30a490a8bb876cd49be68481d
Week 13 news
In the News: http://www.govinfosecurity.com/verizon-confirms-breach-affecting-business-customers-a-8991
Verizon Enterprise Solutions, which regularly assists clients in responding to data breaches, admits it’s suffered its own breach, reportedly affecting 1.5 million business customers. As a result of the exposure of contact information, those customers are now at greater risk of phishing attacks.
Hackers Steal Details of Verizon Enterprise Customers
http://www.securityweek.com/hackers-steal-details-verizon-enterprise-customers
By Eduard Kovacs on March 25, 2016
Eduard Kovacs from Security Week at SecurityWeek.com reports that hackers steal details of Verizon Enterprise Customers.
Verizon Enterprise Solutions is a division of Verizon Communications that specializes in designing, building and operating networks, IT systems and mobile technologies for businesses and governments.
This is a prominent member of an exclusive underground forum that has been offering to sell a database storing the contact information of roughly 1.5 million Verizon Enterprise customers.
The complete database is offered for $100,000, but interested parties can also acquire sets of 100,000 records for $10,000. The seller has also offered information on vulnerabilities in Verizon’s website.
The database is available in multiple formats, including MongoDB. There have been many incidents over the past period where misconfigured MongoDB databases exposed a large number of records of sensitive information.
Verizon Enterprise representatives have confirmed that their website had been plagued by a vulnerability that allowed hackers to steal customer contact information, but has not specified how many are affected. The company noted that the attackers have not gained access to customer proprietary network information or other data. Affected clients will be notified.
“Most companies have a very difficult time managing this issue as it generally falls somewhere between the web team, marketing, regional teams and the security team … and that basically means no one is looking after it. This really is an area where expertise is required and often comes in the form of partnering with experts to manage,”
Capture Files for use in WEP Testing
Caution. This is a big file (48 mb) Only grab it if you want something to run aircrack against.
Week 13?
In the news
Cyber warriors are allowed to have long hair. (UK, not satire)
http://www.telegraph.co.uk/news/uknews/12203745/New-Army-cyber-warriors-allowed-long-hair.html
Week 12: Reading, In The News, and Question
Reading: Aircrack-ng Tutorial: Getting Started, I followed this tutorial, and Tutorial: Is My Wireless Card Compatible referenced, did some additional research and confirmed that my old LINKSYS WUSB600N was compatible with Kali Linux. Referencing our KISMET class notes I was able to access the card from Kali Linux and searched for WiFi access points – and could not find any. This is likely a result of my use of more modern WiFI access points running the WAP2 protocol, and my lack of forethought to purchase a more powerful WiFi antenna like the Alfa cards introduced in class which might have enabled me to find other WiFi access points in my neighborhood. I did run through the injection test and followed the Simple WEP Crack Tutorial, but without a WiFi access point my progress was blocked.
In the News: Node Package Manager (npm) Fails to Restrict Actions of Malicious npm Packages
The CERT Division of Carnegie Mellon University’s Software Engineering Institute reports that a new security vulnerability in the default node package manager (npm) for the Node.js JavaScript runtime server-side web application environment allows packages to take actions that could enable a malicious npm package author to create a worm that can spread as users install node packages and compromise the majority of the npm ecosystem. CERT Vulnerability Note VU#319816 (March 25, 2006) describes the security issue, how the worm works, and provides reference to Sam Saccone’s original research into the vulnerability. While a practical solution to the problem has not yet been formulated, three risk-reduction workarounds are provided which should be considered by application developers using npm in node.js based web application systems they are developing for their clients or organizations.
http://www.kb.cert.org/vuls/id/319816
Question for Class: Does someone with some relevant work experience have interest in helping me develop and deliver a 1/2 day workshop for the Urban Regional Information Association introducing Cybersecurity to managers of Geographic Information Systems at their October conference in Toronto?
Week 12 – Summary
Readings:
Aircrack-ng tool set is very powerful when it comes to wireless transmissions Monitoring, Attacking, Testing and Cracking. It is available in different suite options, such as: VM, Live CD and installer for linux OS. While LiveCD and VM versions are simpler to use, these packages have limitations and vulnerabilities. So, the best option is to use Suite for Linux OS, run suite within Linux environment to take full advantage of all functions; however, it would require deep knowledge of Linux. Aircrack can be used to crack WEP passcode using basic approach of capturing Initialization Vectors and then injecting collected IVs into packets via ARP Replay mode.
Question to the Class:
Is it worth it to write your own DLL for Windows in order to manually link drivers for aircrack to work? Would it not be more beneficial and easier to learn Linux, thus gaining more useful and broad experience?
In the News:
Mac OS X Zero-Day Exploit Can Bypass Apple’s Latest Protection Feature
A critical zero-day vulnerability has been discovered in all versions of Apple’s OS X operating system that allows hackers to exploit the company’s newest protection feature and steal sensitive data from affected devices.
http://thehackernews.com/2016/03/system-integrity-protection.html
P.S. After reading this news, I updated my Apple products right away!
Week 12 Takeaways
Assigned Reading:
Aircrack-ng Suite should be used in a Linux environment and not in a Windows OS since there is not much support for it. For someone who has not been previously exposed to this tool, the simplest process is as follows: determining the chipset in the wireless card, determining which of the three options can be used to run the aircrack-ng suite, and getting starting to use this tool. It is important to properly determine the wireless card chipsets since it needs to be compatible with the aircrack-ng suite. Once that first step is complete, then the user can choose the best option to run that suite. There are three various methods that can run this tool, such as in Linux, a live CD, or a VMWare image.
Question for the class:
What are your experiences thus far running the aircrack-ng suite? What is your preferred method to run it and why?
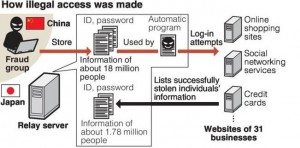
In the news: “18 million stolen IDs discovered on server/criminals in China got illegal access”
The IDs and passwords of about 18 million Internet users have been found on computer server set up by a company named Nicchu Shinsei Corp. in Toshima Ward, Tokyo. The police alleged that the company had provided its customers in China with other people’s IDs to allow them illegal Internet access. The company’s president and other staff were arrested and indicted. The victims were users of major Internet search engine Yahoo Japan, online shopping giant Rakuten, Twitter, Facebook, credit card company Mitsubishi UFJ NICOS Co. and others. It is important to note that the illegal access were conducted from June to November 2015 and the Nicchu Shinsei’s server was used to illegally send money via the Internet banking systems of more than 10 financial institutions.
For more information on the above article, please click here.
Week 12 Reading Summary, Question, and recent Cyber Security News…
- Summarize one key point from each assigned reading…
Aircrack-ng.org published an online tutorial regarding the setup of Aircrack-ng (mostly Linux-based wireless networking suite of digital tools [packet sniffer & injector, WEP & WPA/WPA2-PSK cracker & analysis apps] for ethical hacking purposes on one’s owned networks [not other’s networks.])
- Question to classmates (facilitates discussion) from assigned reading…
Question: During the Aircrack-ng setup, did you confirm that your computer’s networking card can inject packets via the Injector Test?
Identify, read, and post to our blog a current event article regarding ethical hacking & penetration testing (follow theme topic of the week, or other interesting related article)…
In the Cyber Security News lately…
Temple University’s on-going digital battle with Phishing email scams with linked Malware & vigilant solutions (example info from recent email attacks on 3/21/2016 at Temple University)…
—————————————————————————————————————
From: NoReply Delivery Notification [mailto:notification-delivery@xxxxxmail.com]
Sent: Monday, March 21, 2016 8:32 PM
To: XXXXX XXXXX <xxxxx@temple.edu>
Subject: Delivery Tracking Information and ETA – see attached invoice (order # 1562648774)
Attached: USPS_DELIVERY_TRACKING_AND_ETA.doc
USPS.com Order #: 1562648774
Hello,
Thank you for your order.
See the attached invoice for package tracking information and estimated time of arrival.
Order #: 1562648774, Placed on: March 18, 2015 9:30:00 AM, Status: Order Placed, Ship to: See attached invoice
—————————————————————————————————————————————————————-
*NOTE: Computer users just had to open the file attachment within this email example, and next a Trojan.Dropper began an install process on client’s Windows PC!
**NOTE: Some of the vigilant solutions examples at Temple University, Computer Services (TUCS) included the following:
- notification-delivery@xxxxxmail.com was blocked in Temple-Firewall, etc.
- Symantec Endpoint Protection (SEP12.1.6.x Enterprise) with latest SEP definitions did detect & quarantine Trojan.Dropper malware (USPS_DELIVERY_TRACKING_AND_ETA.doc)
- TUCS-Client Services then further checked & removed any further Trojan.Dropper malware via SEP12.1.6.x, Malwarebytes in Windows-SafeMode, etc. on reported infected Windows client PCs.
- TUCS continued to educate it’s networked computer users via official Temple University email regarding latest & future Phishing email scams, etc.