-
Binu Anna Eapen wrote a new post on the site IT Audit Capstone 7 years, 5 months ago
Please complete your 50 quiz for chapter 3 before Mon 5/22/2017 and post your results in this site.
-
Binu Anna Eapen wrote a new post on the site IT Audit Capstone 7 years, 6 months ago
Please complete your 50 quiz for chapter 3 before Mon 5/15/2017 and post your results in this site.
-
Binu Anna Eapen wrote a new post on the site IT Audit Capstone 7 years, 6 months ago
Please complete your 50 quiz for chapter 2 before Wed 5/13/2017 and post your results in this site.
-
Binu Anna Eapen posted a new activity comment 7 years, 6 months ago
32/50
-
Binu Anna Eapen wrote a new post on the site MIS5208 Spring 2017 7 years, 6 months ago
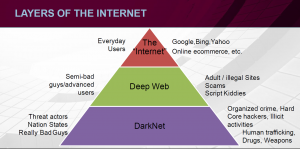
Based on accessibility Internet can divided into 3 layers.
Clear Web or The internet is the surface area indexed by search engines like google, bing, yahoo, facebook etc.
Deep web is a subset of the […]
-
Binu Anna Eapen wrote a new post on the site MIS5208 Spring 2017 7 years, 6 months ago
Big Data is collection of petabytes of data. Cyber security today has to deal with this large amount of disparate data collated from around the enterprise into centralized dashboard which could be in Network […]
-
A major focus of the user studies was to identify challenges in cyber security to explore how visualizations may enable users to meet those challenges. There was not a prescribed set of challenges that users chose from, instead challenges were compiled from study results and then validated with cyber SMEs. Some of these challenges are not surprising, involve the “big-data” problem (velocity, volume, and variety), and have been previously documented in the literature. However, other identified challenges hold opportunities for further research in visual analytics to enhance the abilities of the personnel defending our networks. By understanding the challenges faced by cyber defenders, a visualization can be designed to help address them, increasing
the tool’s usefulness for the user.
-
-
Binu Anna Eapen wrote a new post on the site MIS5208 Spring 2017 7 years, 7 months ago
The article provides an in-depth overview of the use of data analytics technology in public sector. The focus is given to how data analytics is being used in the government setting. The ability to interpret the […]
-
Binu Anna Eapen wrote a new post on the site MIS5208 Spring 2017 7 years, 7 months ago
Last week in class we had discussed about the 3 characteristics of analytical dataset which are the 3 V’s of big data – volume, velocity and variety. In this article the writer adds 3 more V’s that IT, bus […]
-
Binu Anna Eapen wrote a new post on the site MIS5208 Spring 2017 7 years, 7 months ago
The driving factor for most cyberattacks or cyber-crime is money. Ransomware is a type of malicious software designed to block access to a computer system/ file until a sum of money is paid. Though the concept of […]
-
Binu Anna Eapen wrote a new post on the site MIS5208 Spring 2017 7 years, 7 months ago
A Star Trek themed ransomware named Kirk written in Python targeting 625 different file types has emerged and the attacker are demanding ransom to be paid in virtual currency Monero. The threat is paired with a […]
-
Binu Anna Eapen commented on the post, Progress Report for Week Ending, March 1, on the site 7 years, 8 months ago
Thanks David for sharing your experience. I think the human element to these frauds makes it easier and vulnerable for an attacker to make his/her move. Human has always been the weakest link to security. However secure the system is, it still remains vulnerable to such frauds. It is a good practice to educate users and customers and making them…[Read more]
-
Binu Anna Eapen wrote a new post on the site MIS5208 Spring 2017 7 years, 8 months ago
This report talks about PSCU’s (Payment Solution for Credit Union) proactive partnership to fight against call center fraud. Call center fraud is the act of a criminal impersonating a consumer via a phone channel […]
-
Thanks David for sharing your experience. I think the human element to these frauds makes it easier and vulnerable for an attacker to make his/her move. Human has always been the weakest link to security. However secure the system is, it still remains vulnerable to such frauds. It is a good practice to educate users and customers and making them aware of this like in the case of Barclay because of which you were able to identify and not be cheated.
-
-
Binu Anna Eapen wrote a new post on the site MIS5208 Spring 2017 7 years, 8 months ago
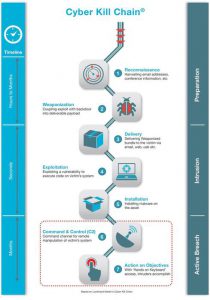
This model shows a common cycle that the attackers use to exploit an organisation. An understanding of this model can help organisation to protect, detect, identify, respond and recover when the organisation is […]
-
Binu Anna Eapen posted a new activity comment 7 years, 8 months ago
Nice post Alexandra. With the rise of the concept of big data where in large amount of data is stored and then analyzed for various purposes like finding trend, understanding the customer, or understanding markets, knowing the organization and its employees, it can also be used for analyzing risks, monitoring and identifying threats, More data…[Read more]
-
Binu Anna Eapen posted a new activity comment 7 years, 8 months ago
Nicely written Deepali. As mentioned Advertising and marketing are two areas that the Big data is very useful. Big data has made the market more customer oriented and helps with the following
1. To understand the customer: We see that Amazon and other sites use the information we browse to advertise to us their similar product as Advers even when…[Read more] -
Binu Anna Eapen commented on the post, Week 03 – Discussion Question 2, on the site 7 years, 8 months ago
I agree with you that deep and detailed knowledge about a particular technology can waste excessive time on irrelevant and negligible subjects. But knowing it won’t hurt either. It depends on how he uses the knowledge that he/she has for the audit. Also the perspective of which is important: depth of knowledge or impact on the business depends on…[Read more]
-
Binu Anna Eapen commented on the post, Progress Report for Week Ending, February 23, on the site 7 years, 8 months ago
I agree with you Blake that the Millennials have a great advantage of having to grow up with the technology. They are quick to learn and well educated. They are ready for change and ready to challenge the norms as you said. All these qualities are traits of a good Auditor or Assurance Professional. One thing that Millennial lack is experience and…[Read more]
-
Binu Anna Eapen posted a new activity comment 7 years, 8 months ago
Technology has been ever growing and most often it is a decision that the management has to make whether to incorporate it into the system or not.
I guess the answer to this question depends who you are in an organization. For example, if I am an application developer, I will be concerned with learning new technologies so as to be in market and…[Read more] -
Binu Anna Eapen posted a new activity comment 7 years, 8 months ago
While the traits mentioned by Dr. Ed Glebstein, Ph.D in his article “Is There Such a Thing as a Bad Auditor” are all undesirable traits of an auditor, in real time we do see such characteristics come by due to the fact that Auditors are also human prone to different behavior. Reading this article one can be aware of their behavior type and mak…[Read more]
-
Binu Anna Eapen posted a new activity comment 7 years, 8 months ago
Nice post Alexandra. Lying about your knowledge can be very risky especially because the auditee would most likely be an expertise in that field and would very easily find out if you are lying or not. Not only that it is difficult to fake knowledge for a longer period of time. The Faker can therefore incorrectly determine the risks as he may not…[Read more]
- Load More
Connect and innovate with an elite information systems program
Footer
MANAGEMENT INFORMATION SYSTEMS
Fox School of Business
Temple University
210 Speakman Hall
1810 N. 13th Street
Philadelphia, PA 19122

Domain 3 quiz 3
44/50
88%
Domain 3, Quiz 2: 82%
72%