-
Priya Prasad Pataskar posted a new activity comment 7 years, 7 months ago
70%
-
Priya Prasad Pataskar wrote a new post on the site MIS5208 Spring 2017 7 years, 8 months ago
James has mentioned a pretty interesting trend in his post, Predictive analysis. I wanted to add the neat diagrams I came across and hence I am adding a new post rather than commenting. And as I understand since […]

-
Priya Prasad Pataskar wrote a new post on the site MIS5208 Spring 2017 7 years, 9 months ago
Kill Chain is a military concept relating to the structure of launching an attack. The word chain comes from the fact that if the process or steps are broken at a stage the model the entire model breaks. It is a […]
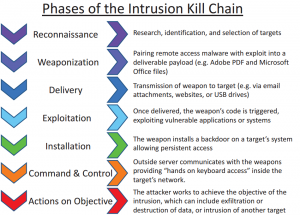
-
Priya Prasad Pataskar wrote a new post on the site MIS5208 Spring 2017 7 years, 10 months ago
I did some research on how easy or hard it is to spoof someone’s phone number and let you believe that you are getting a call from someone at your office, a future recruiter, a person you know friend or r […]
-
I had never really considered this until reading your post. I could see this being a valuable tool for debt collectors. Since laws have been passed that now penalize debt collectors if they contact your place of employment or your neighbors they have had to find other more creative ways to contact and/or harass their targets. Since debt collectors know they will likely face avoidance when contacting the debtors they would find a lot of value in using this easy spoofing technology. I could see marketers finding this type of tool valuable as well since many people avoid unfamiliar numbers. This type of tool, and its uses, would be most beneficial with a list of known numbers associated with the target so a number is used that increases the likelihood of being answered.
-
Nice post, Priya. I think you shared you experience with phone number spoofing this week, which i thought was quite dangerous, honestly. I was researching if there are any methods/applications through which we can protect ourselves from such ordeal but unfortunately all my research pointed me towards making our brains scam-proof. What I mean by that is just making a habit to not conduct any business over the phone and always restrict yourself from giving your personal information to the caller. Some of the red-flags are the IRS Scam calls, since IRS will never call you and it’s just another scare tactic. There are also red flags right, someone offering you a deal that is too good to be true or by using words like “Don’t miss out or hurry up!” I think we just have to make a personal rule that if you are not sure of the caller’s identity just tell him/her that you will call back.
-
-
Priya Prasad Pataskar wrote a new post on the site MIS5208 Spring 2017 7 years, 10 months ago
TBML is most sophisticated means of cleaning dirty money. IT is a way to legitimate the illicit origins. People involved in this scheme use a legitimate business or trade to disguise the criminal act. Simple […]

-
Priya Prasad Pataskar wrote a new post on the site MIS5208 Spring 2017 7 years, 10 months ago
Organisations reports breaches and invests time, talent and millions of dollars to investigate the fraud. This is not a one off activity but a continuous improvement process. A model to investigation reporting and […]
-
Nice post Priya. Regarding the flow diagram point, I’m totally agree that having very clear and comprehensive flowchart that represent the workflow in an organization is very helpful way to detect and prevent the fraud since this workflow is comprised of the set of process it needs to accomplish connected with the people who responsible to perform those process, and the interaction among them. Thus, this will assist to discover the errors and the person who make it occur.
-
Nicely said Priya, I really like that you mentioned that every breach is a learning. Indeed, the least companies can do is to learn lessons from incidents to help ensure the same thing doesn’t happen again. Additionally, it is really important to detect breaches early in the process to minimize losses. I believe businesses must build a system that can automatically detect every form of attack and fully be prepared.
-
Nice post Priya, apart from what you mentioned, I believe that the adaptability is also one essential part of a successful fraud investigation. After making a plan, and then you make sure the plan is carried out. You will almost certainly have to change the plan as you go along. Perhaps an even better analogy is a military campaign, as in war, success goes to the side which adapts best when circumstances change or things go wrong.
-
-
Priya Prasad Pataskar commented on the post, Progress Report for Week Ending, February 23, on the site 7 years, 10 months ago
I agree with you Yu Ming. Depth and impact are both are supportive of each other. The speed with which new technology emerges is so fast that while gaining depth of one technology world moves to another. I do not know what is the best solution but I believe experience teaches it all. Hence before making a new technology active in the business, it…[Read more]
-
Priya Prasad Pataskar commented on the post, Progress Report for Week Ending, February 23, on the site 7 years, 10 months ago
Good point Annamarie. I have mentioned in my post that transition to new technology must be smooth, and thus the impact will be managed. Any new technology will have similarities with what employees are familiar with. Organization can make a choice of smooth transition. It is also necessary to help by giving time and exposure to the new technology…[Read more]
-
Priya Prasad Pataskar posted a new activity comment 7 years, 10 months ago
Hi Candace, Thank you for providing links to interesting articles, I read a few of them and Meyer in his article mentions that switching between activities will prove a hindrance in productivity.
However, I feel today’s tasks, professional activities, machine usage requires multitasking. Our brain is adaptable and is hopefully adapting to this…[Read more] -
Priya Prasad Pataskar posted a new activity comment 7 years, 10 months ago
Behavior of generation reflects in workplace. Companies face bigger problems that downsizing,
problem of workflow balance between the Baby boomers, X and Y and Veterans. Audit as a profession goes by 80:20 rule. 20% auditing technicalities and 80% communication and behavior during audit and towards auditee.
Millennial generation they say is…[Read more] -
Priya Prasad Pataskar posted a new activity comment 7 years, 10 months ago
IT audit values independent skilled assessment of risks and controls. As an IT auditor it is important that you evolve as the industry is evolving. True traits of an auditor are clearly seen through the auditor’s experience, education and most of all his behavior traits as a human being. Ed Gelbstein, Ph.D.in his article “Is there such a thing as…[Read more]
-
Priya Prasad Pataskar posted a new activity comment 7 years, 10 months ago
Great post Magaly. The Lazy type can yield a absolute wrong result. They would be dependent on previous documentation, or worst the previous report and do a copy paste.
However with this kind, the audit report reviewer or senior auditor will easily catch hold of him and his mistakes. It is very difficult to justify why have you included an…[Read more] -
Priya Prasad Pataskar posted a new activity comment 7 years, 10 months ago
Great post Candace! I totally agree with your comments about the Stress creator type.
According to study conducted by Richard Lazarus, stress goes to various appraisal levels and influences specific type of performance. At secondary appraisal, the person begins to think what he can do his best to lower the stress. A moderate level stress in fact…[Read more] -
Priya Prasad Pataskar posted a new activity comment 7 years, 10 months ago
Paul, this is a well defined issue. In continuation to your article I read a post by EY which spoke about strengthening the SOD control. They suggest to take a risk based methodology for SOD. What companies should figure out is the conflict with the. A task based SOD is costly and this division does not effectively handle SOD control. Companies…[Read more]
-
Priya Prasad Pataskar wrote a new post on the site MIS5208 Spring 2017 7 years, 10 months ago
Fraud has repercussions far more than just financial losses. Fraud does not stop on its own unless it is detected and stopped. People find ways to continue fraudulent activities even after getting caught. Serious […]
-
Priya Prasad Pataskar wrote a new post on the site MIS5208 Spring 2017 7 years, 10 months ago
Are existing security approaches failing to defend against sophisticated cyber-attacks? Most organizations have layered security, firewalls, intrusion detection, incident response teams and data loss prevention […]
-
Priya Prasad Pataskar wrote a new post on the site MIS5208 Spring 2017 7 years, 10 months ago
Hello everyone, I am a full time ITACS student in the IT Audit track and plan to complete the course this summer. Currently I work as a Information Security intern at Temple University. I enjoy working in both […]
-
Priya Prasad Pataskar posted a new activity comment 8 years ago
Said, I think when i comes to audit, management would be fine and good to hide some facts, but when a breach would happen no one would be spared. In fact the auditor would the one who would be questioned.
I agree that in some cases, nothing can be done but accept the risks. In such cases, it should be documented that the risk is accepted or there…[Read more] -
Priya Prasad Pataskar posted a new activity comment 8 years ago
Sean, you mentioned about integrating controls while system is implemented. Definitely that is the time when system is new and ready to take in changes as less or no data is present. However I think the need for more controls would arise as company grows and the process becomes mature. Unless the process is explored in depth, employees may not be…[Read more]
-
Priya Prasad Pataskar posted a new activity comment 8 years ago
Well said Binu. I think automated controls should be in place to strengthen the system. How much ever manual controls you make, as humans we are prone to errors, importance must be given to automate most of the controls. Except for those which need judgement based decision making. The important thing is to train employees to ensure they know what…[Read more]
- Load More
Connect and innovate with an elite information systems program
Footer
MANAGEMENT INFORMATION SYSTEMS
Fox School of Business
Temple University
210 Speakman Hall
1810 N. 13th Street
Philadelphia, PA 19122
