Amazon Cloud
http://www.computerworlduk.com/news/it-vendors/amazon-cloud-to-host-erp-software-19693/
This article talks about how Amazon’s Cloud is to host ERP software. Lawson software announced a partnership with Amazon. This will allow people to have a test drive for up to two weeks and you can use your own data and business processes. He proposes that he will not price the cloud to high. The sole purpose of the software is not to gain market share. People will be able to convert over to a subscription after the free trial is over. Lawson is a very popular ERP vendor who works with Oracle, SAP, and Microsoft.
1. Do you think it’s a good idea to give this software a trial run?
2. Do you think offering the trial run will lose revenue for Lawson because people may not subscribe?
3. Do you think Amazon is a good contender for this new software?
Five signs you should consider outsourcing your IT
http://www.bizjournals.com/boston/feature/5-things/2015/06/five-signs-you-should-consider-outsourcing-your.html?iana=ind_tech
One of the topics discussed in chapter 9 is acquiring information systems. The book explains how companies acquire information systems from outsourcing. In the article, “Five Signs You Should Consider Outsourcing Your IT”, written by Diego Rosenfeld, the author talks about when the companies should consider outsourcing some or all of the components of their IT function. The reasons that companies are outsourcing IT function is to save money, improve performance, add scalability, and get access to strategic IT thinkers. The article points out five signs when the companies need outsourcing
1. Can’t keep up
Broader IT road map includes strategic thinking about issues like how to leverage the cloud and how to select and manage the highest-impact systems and project. Thus, the companies should consider outsourcing when they cannot keep up with technology changes.
2.Anticipating growth
The companies need more diverse IT skill sets as companies grow. Outsourcing will bring the companies broader spectrum of IT skills such as system analysts, database experts, report writers, help desk, system administrators and strategic thinkers.
3.High turnover
There are limited talented IT resources and they are in high demand. For most of the companies, it is hard to retain talented IT resources internally and having only one person with key technical skills creates risk to the business. In the article, Diego says “external provider with scale and a track record of continuity mitigates the risk of a shallow internal resource pool. You’re not just buying a consultant, you’re buying a firm.” Thus, the companies can decrease their risks and increase their opportunities by outsourcing.
4.Performance and stability issues
The companies should consider outsourcing when the companies are having problems in recurring performances and stability issues with critical IT systems. Outsourcing will help the companies in managing IT systems with deeper expertise.
5.Around-the-clock and multi-location coverage
Many companies and their employees run around the clock and the globe, which means that you need IT resources available 24/7 year round and on-site for emergencies. By outsourcing IT, the companies can have service desks that run 24/7.
In summary, there are many inflection points that may lead organizations to outsource some or all of their IT functions, for example:
- Interruptions in service
- Departures of key personnel
- Expansion plans
- New strategic initiatives
As Diego says in the article, modern IT outsourcing providers provide skill, scale and strategic vision to help growing businesses focus on their business while they focus on running the IT foundation that makes it possible.
Questions:
- Is there any other signs that the companies should consider outsourcing services?
- What are the other benefits of outsourcing IT services?
- What are the risks of outsourcing IT services?
7 Top Futurists Make Some Pretty Surprising Predictions About What The Next Decade Will Bring
The article I chose explains what some top futurists think may be the next up and coming technology advances in our society. The futurists are not just any old blogger, they are well-represented physicists, scientists, CEO’s, etc. Some top theories include
-A switch from the internet to the brain-net (where thoughts, feelings, emotions can be shared instantaneous)
-3D printing will be an asset businesses can utilize such as big warehouses that produce a large amount of products
-Virtual and augmented realities will be where we spend a considerable amount of our time.
-Wearable mobile devices will blanket the market.
-Predictive medicine will change health care
-Artificial intelligence becomes as smart and smarter than humans.
All these advances come from the on-demand economy that we live in today. This represents the automation of day-to-day activities can be simplified to make our lives easier. Examples such as Uber, the Amazon tab, etc. Access will trump ownership in the coming years.
The technologies are super cool, but how will they be institutionalized into our society and how society will react to upcoming changes in our technological advancements.
Questions..
1.) What challenges will the ‘brain-net’ bring into the cyber security threats that we are currently starting do deal with as a society?
2.) What benefits may a 3D printer have for a retail business? Or challenges?
3.) How is Cyber Security going to be dealt with when as a society there are new hacking threats and technological advances happening so fast it may be hard to keep ahead?
Video of the On-Demand Revolution..
http://www.huffingtonpost.com/2015/05/12/futurists-next-10-years_n_7241210.html
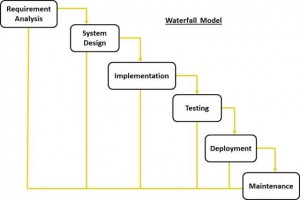
SDLC vs. The Chaotic Evolution of Technology (System Development Life Cycle)
http://www.computerworld.com/article/2576450/app-development/system-development-life-cycle.html
One of the topics discussed in Chapter 9 of Information Systems Today describes the systems development life cycle and its four primary stages:
- Systems planning and selection
- Systems analysis
- Systems design
- Systems implementation and operation
In the article System Development Life Cycle, written by Russel Kay, he mentions a number of system development life cycle (SDLC) models that were developed in order to make it easier to manage todays much larger and complex systems, allowing teams to work more efficiently in parallel.
The oldest and best known of these is the waterfall model, which is very similar to the process described by Valacich. But even though this model is well understood, Kay argues that it’s not as useful as it used to be. In a 1991 Information Center Quarterly article, Larry Runge stated that SDLC “works very well when we are automating the activities of clerks and accountants. It doesn’t work nearly as well, if at all, when building systems for knowledge workers — people at help desks, experts trying to solve problems, or executives trying to lead their company into the Fortune 100.”
Another issue is that the waterfall model operates under the assumption that the only role for users is in specifying requirements, and that the requirements can be specified in advance. The problem here is that requirements grow and change throughout the entire process, which calls for extensive feedback and iterative consolation.
As a result of trying to solve these types of issues, these others SDLC models have been developed: waterfall, fountain, spiral, build and fix, rapid prototyping, incremental, and synchronize and stabilize.
Questions:
1. Can you recall something you’ve heard or read where a company applied some sort of SDLC?
2. Do you think more complex models of SDLC will be introduced with technologies fast paced evolution?
3. Can you think of an example of any positions or industries where the water fall module would not be suitable?
Development of Mobile Applications
http://www.theguardian.com/media-network/2015/feb/13/history-mobile-apps-future-interactive-timeline
In Chapter 9, we learned about development and acquiring information systems. One form of this that affected nearly all of us over the past 22 years is the development of mobile applications. Below I listed a timeline, which I acquired from the article listed above, of just a few examples of the development of mobile applications from 1983 until today.
June 1983: Steve Jobs predicts a software distribution system at a conference in Aspen. He was quoted as saying “the future isn’t what it used to be”
January 1987: The Psion EPOC was released. This handheld computer used an operating system, which had basic applications such as a diary.
August 1993: Apple created the Newton MessagePad which contained built in apps such as web, e-mail, calendar, and address book.
November 1993: A Business Week article predicts “the future information appliances will instantly make the connections to a world of digitalized entertainment communications” and data on the superhighway or over the airwaves.
December 1997: The Nokia 6110 made an appearance. This device was the first phone to posses the game “Snake”, setting the bar for mobile games.
October 1999: Wireless Application Protocol (WAP) was introduced. This allowed users to access information over a mobile wireless network for the first time.
October 2001: Apple releases the first IPod that included apps such as solitaire and brick and offered “1,000 songs in your pocket”.
April 2003: Apple launches the ITunes Music Store., 1 million songs sell in the first week.
June 2007: Apple announces that developers can create Web 2.0 applications, which look and behave just like the applications built into the IPhone.
June 2007: The first IPhone is launched. 270,000 phones sold during the first 30 hours of sales.
July 2008: The App Store is launched. Originally there were 552 apps total and 135 of them were free.
September 2008: Apples App Store reaches 100 million downloads.
October 2008: Google’s Android market is launched. This would become Apple’s key rival.
April 2009: Blackberry World is launched. It becomes the third major distributor of mobile applications.
December 2009: Angry Birds is launched. Angry birds would go on to become the best-selling paid application of all time. It would also go on to reach 1 billion downloads.
October 2010: Windows Phone Store is launched and becomes the fourth major distributor of mobile applications.
January 2011: The word “app” was voted word of the year for 2010.
March 2011: Amazon App Store is launched.
June 2011: Zynga Games lose 36 million users since 2012. This is a clear sign that consumers are shifting to games found on mobile devices.
December 2011: Apple reveals that the app revolution has added more than 291,250 jobs to the U.S. economy since the introduction of IPhone in 2007.
April 2012. Facebook acquires Instagram. With a price tag of $1 billion, this is currently the highest ever paid for an app company.
November 2012: Candy Crush is released and would become the most downloaded application of 2013.
May 2013: Apples app store reveals its top downloads list. Angry Birds tops the paid list while the Facebook app tops the free downloads.
June 2013: Universal’s Despicable me app makes the top ten list for 2013 showing traditional media moving towards mobile applications.
July 2013: Previously known as the Android Market, Google Play has more than 50 billion downloads.
January 2014: 1.75 billion smartphones are predicted to be used around the globe. Data from Nielsen shows that U.S. users of smartphones spend 65% more time each month using apps than they did just two years ago.
May 2014: After rejecting Facebook’s $3 billion offer, Snapchat continues to be a rising app sharing over 700 million photos everyday.
June 2014: App Store reaches 75 billion downloads.
September 2014: 20.3% of App Store downloads are games, with 10.36% educational apps and 1.9% social networking
1. What event listed above do you believe was the most important in regards to the development of mobile applications?
2. What is your most used, and favorite mobile application?
3. Do you have any visions of what mobile applications may evolve into in the future?
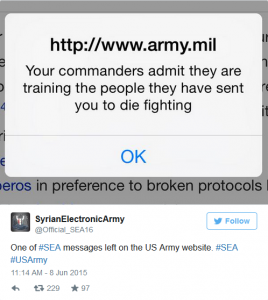
The Evolving Challenge of Cybersecurity
http://www.cbsnews.com/news/the-evolving-challenge-of-cybersecurity/
Chapter 10 of our text starts off by describing the various security threats that can occur on information systems and the importance of engaging in IS risk management as computer criminals and their crimes increase. Valacich also mentions that the US government is one of the most targeted organizations for hackers and crackers that are looking for information. A recent article from CBS News highlights this concerning topic as the government seeks a remedy in their latest cyberattacks. It has been disclosed that the US Army’s website was victim to a hacking claimed to be by the Syrian Electronic Army. Upon entering the website, a pop up message was displayed that read “your commanders admit they are training the people they have sent you to die fighting.” However, as soon as the government became aware of the breach, the website was quickly taken down for repair.
The accompanying video with the article includes an in-depth discussion of this topic as well the vulnerabilities that come with cloud computing and ways to improve our cyber security when doing business online. It is important to note that the government is not the only entity at risk. With an increasing trend in hacking and technology advancing towards cloud computing, many new security threats will enter consumers’ daily lives. Keeping files on a cloud makes it easier for hackers/crackers to obtain personal information, therefore it is crucial for everyone to maintain cybersecurity. Some of the methods discussed include using only one credit card to make online purchases and regularly changing the passwords to important accounts.
1. Chapter 10 states that “a cyber cold war is an imminent threat for the world’s computers.” Do you think the recent news of the attacks against the government foreshadows an increase in cyberwar and cyberterrorism?
2. Have you ever been a victim of a cybercrime? If so, how has it changed your outlook on the use of the internet?
3. What do you think is the most important thing for individuals or the government to do to improve cybersecurity?
Financial Firms Grapple With Cyber Risk in the Supply Chain
http://blogs.wsj.com/cio/2015/05/25/financial-firms-grapple-with-cyber-risk-in-the-supply-chain/
This article talks about the growing concern for cyber risk in the business world. With technology advancing so quickly, companies are now faced with the challenge of keeping their data and information safe from hackers. Since the business world is so interconnected, with intricate supply chains and partnerships, companies are becoming more and more vulnerable to a hack. For a supply chain to function seamlessly, all participants must use compatible computer systems. Some firms have lagging cyber safety protocols in place because an update would cause a break in the supply chain. This article cites an example of a Fortune 500 bank whose system is not patch for a bug called “Heartbleed”, and remains this way because patching their systems would break continuity with many European banks that have not updated their systems. Companies are forced to choose between a system safe from hackers and a continuous supply chain, which proves to be a tough decision. Regulators have created cyber safety and protection standards for firms in the US to avoid major hacks and breaches to precious information.
1. Do you think firms are going to be forced to break continuity in their supply chain to maintain safety standards in regards to cyber risk?
2. Do you think the regulators will be successful in enforcing their rules and standards, and how do you think they will do this?
3. If you were faced with the decision of a continuous supply chain or comprehensive cyber safety, which would you choose? Why?
The Pros of Using System Analysis & Design for Your Business
This article by Vicki Benge highlights the benefits of systems analysis for improving the overall quality of a business. In a sense, it is a summary of Chapter 9 from “Information Systems Today,” and ties in elements previously discussed. Generally, systems analysis is used to improve the efficiency and effectiveness within a business’s boundaries. One instance in which systems analysis can be implemented is for enabling the customization of software to better fit the needs of a firm. It also allows for improvements in weaker areas, including data processing. Second, it increases their competitiveness in their industry. Establishing a global market is a very common practice, and is sure to increase their “market coverage area” and profits through the implementation of ecommerce. Third, systems analysis can help identify new markets and opportunities leading to new procedures and increased quality. Finally, systems analysis helps maintain quality control while decreasing production costs.
Discussion Questions:
1. Which of the benefits of information systems do you think is most crucial for a business?
2. How do the benefits of system analysis and design differ from the benefits of ERP?
3. How does ERP relate to the motives of systems analysis and design?
Who’s Really at Risk When it Comes to Cyber Hacking?
http://www.propertycasualty360.com/2015/05/27/small-mid-sized-businesses-hit-by-62-of-all-cyber
This article debunks the notion that large businesses are targets of hackers. Everyday we see the media covering more and more cyber attacks that involve large corporations. This is a huge problem because it insinuates the notion that small businesses are safe from the hacking of their Information systems. The ones that go unnoticed are the small healthcare and financial institutions that get hacked everyday in the United States. The article talks about how 62% of cyber breaches involve small to mid-sized companies. It also goes on to state that 34,529 known computer security incidents happen per day in the U.S.
In a sense, it’s almost a feeding frenzy for these hackers because either the small businesses that they’ve hacked don’t know they’ve got hacked or they try to sweep it under the rug and pretend that it didn’t even happen. Until these businesses start to realize they are the real targets, they will continue to take on the majority of the hacking that goes on in the United States. Once they start implementing the preventative measures needed to mitigate the risks of cyber attacks, I truly believe these staggering numbers will drastically reduce.
1. What do you think Small to mid-sized businesses need to do to mitigate the risk of getting hacked?
2. What can lawmakers do to help contain the ever growing problem of cyber attacks?
3. Do you see cyber risks as an ever-growing problem for corporate America and if so, where does it rank it terms of problems that these companies face?
Using a private cloud to keep the coffee on at Dunkin Donuts
This article discusses how National DCP, a major supplier of Dunkin Donuts, integrated a private cloud system after the company had underwent a large merger. It all started in 2012, when four regional Dunkin Donuts suppliers merged to create a company called National DCP LLC. When the company was initially created, each regional operation kept its own system running and the new corporation started its own. Darrell Riekena, the CIO of National DCP, decided that the company needed to move to the cloud to fix this situation. National DCP wanted not just to integrate their systems but to integrate them all on a private cloud, giving them the security, reliability and scalability they needed without having to build them out and manage all of them on their own.
The Business
National DCP, based in Duluth, Ga., services more than 8,000 Dunkin Donut locations in 51 countries. When the four businesses merged it left them without a unified IT system. Riekena was hired in 2013 and began working with 28 members of the company’s IT team on the project, however they would come to learn that the project required a greater work force.
The Team
Riekena decided to use Verizon Communications’s private cloud and also brought in consulting giant Deloitte to serve as their integration partner.
Beginning the Integration
By the end of 2013, the team had an integration plan in place, had assessed all of their applications, and had created a business plan. In January 2014, they began the project, working on the system configuration and plotting how the implementation of the plan (Project Fresh Start) would go. In October 2014, National DCP launched the first of four phases of its IT merger, integrating the Southeast region’s system with the corporate system, and it was a big success. With the success of the first region, the company plans to continue integrating the remaining regions. The mid-Atlantic region is set to be the last region integrated and is scheduled for the first quarter of 2016.
Questions –
1. If you were the CIO would you have chosen to move to the cloud as well or would you taken the company in a different direction following the merger?
2. Do you think it was necessary to bring in Deloitte as a partner or could National DPC have successfully completed the integration process on their own? What are some of the benefits to bringing in a partner like Deloitte?
3. In the future, do you see the cloud becoming a popular choice for other companies going through a merger?


Recent Comments